
APIs (Application Programming Interfaces) are the backbone of modern technology, connecting apps, services, and devices behind the scenes. They power everything from online payments, SaaS tools, to cloud storage. While APIs make things easier in the developing digital world, it does not come without risk.
When APIs are not properly secured, they become the primary target for cybercriminals. They can expose sensitive data, give them unauthorised access, or even allow for company-wide breaches. This is not just a theoretical risk, it is happening right now!
Recent research by Truffle Security found nearly 12,000 hardcoded API keys, passwords, and credentials openly available on public web pages. This data leak was found when they scanned Common Crawl - a training dataset used by LLMs (Large Language Models) like DeepSeek.
Among the leaked API keys, 1,500 unique Mailchimp API keys were found which attackers could use for phishing campaigns, data exfiltration, and brand impersonation. Beyond being a security threat, these kinds of API data leaks can cause serious financial and reputational damage to companies that can be hard to overcome.
📋 Quick Summary in 60 Seconds
API Security Overview:
Threat protection: Safeguarding APIs from injection attacks, broken authentication, data breaches, and unauthorized access through comprehensive security measures
Access control: Implementing robust authentication mechanisms like OAuth 2.0, JWT tokens, and role-based access control to verify user identities and permissions
Traffic management: Using API gateways to centralize security policies, enforce rate limiting, and monitor suspicious activity across all endpoints
Data encryption: Securing sensitive information through HTTPS protocols, encrypting data at rest and in transit, and proper key management
Why API Security is Crucial?
Prevents catastrophic breaches: API attacks surged by 3000% in 2024, with 95% of IT professionals experiencing production API problems that led to data exposure
Ensures regulatory compliance: Strong API security helps meet standards like GDPR, HIPAA, and PCI-DSS while protecting customer trust and brand reputation
Maintains business continuity: Prevents service disruptions from DDoS attacks and unauthorized access that can cost millions in downtime and recovery
Top Pain Points:
Shadow API proliferation: 90% of organizations host undiscovered shadow APIs that expand attack surfaces and create blind spots in security coverage
Authentication vulnerabilities: Broken authentication and weak access controls expose sensitive data, with 30% of critical API vulnerabilities remaining unpatched for months
Scale management complexity: Growing API ecosystems make it difficult to maintain consistent security policies and monitor threats across distributed services
How DigitalAPI Helps:
Centralizes security governance: Provides unified API management that enforces consistent authentication, authorization, and monitoring policies across all endpoints
Automates threat detection: Implements real-time monitoring and advanced analytics to identify suspicious patterns and prevent attacks before they cause damage
Streamlines compliance: Delivers enterprise-grade security controls and documentation that simplify regulatory compliance and audit requirements
Final Note
API security isn't just about preventing attacks—it's about building a foundation of trust that enables digital innovation. With cyber threats evolving rapidly and APIs becoming the primary attack vector, organizations need proactive security strategies that protect sensitive data while enabling seamless integrations and business growth
What is API security?
API security is the practice of protecting APIs from unauthorised and unauthenticated access and misuse. The practice involves methods like securing authentication, authorisation, data transmission, and endpoints to prevent threats like API leaks, injection attacks, and DDos attacks.
Importance of API security
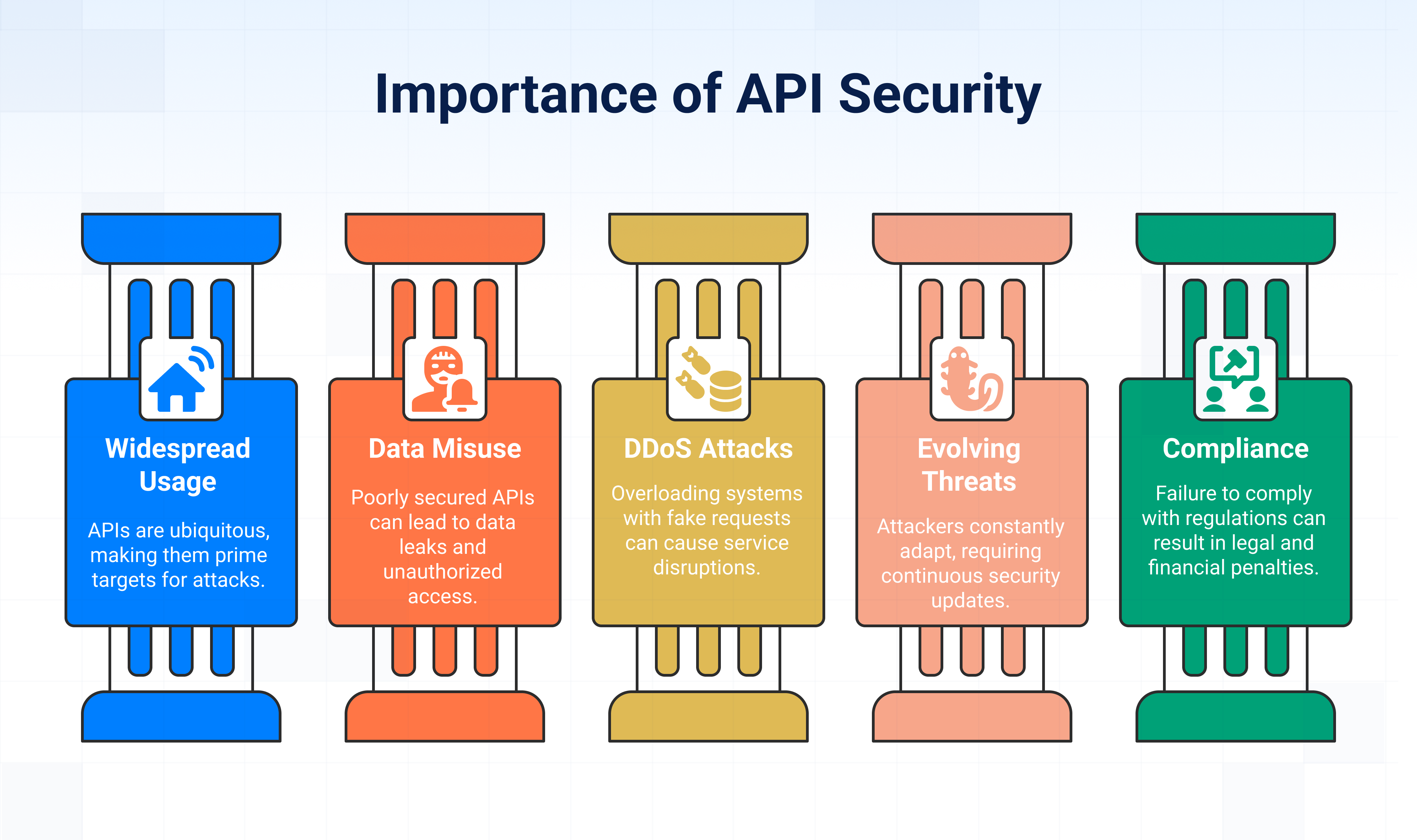
1. APIs are everywhere
According to Imperva’s 2024 API Security report, 71% of all web traffic is API-related with an average of 1.5 Billion API calls made to enterprise sites per year.
This widespread usage of APIs make it a high-value target for attackers constantly looking for holes in the API security. Every API call is a potential entry point for hackers trying to steal data, inject malicious code, or exploit business logic.
2. Prevent API misuse
APIs frequently handle sensitive information, including customer records, payment details, healthcare data, and other confidential information. When APIs are poorly secured, attackers can easily:
- Leak sensitive data like customer information, banking information, and financial records.
- Exploit authentication flaws to gain unauthorized access.
- Inject malicious requests that manipulate backend operations.
For example, in 2021, T-Mobile suffered an API breach that exposed more than 76 million customer records including names, emails, and phone numbers. The attackers exploited an API vulnerability to access the data without authentication.
3. Prevent DDos attacks
While API misuse leads to data leaks and manipulation, attacks like DDos or Distributed Denial-of-Service attacks overload and crash the system completely. DDos attacks happen when attackers flood the system with fake API requests. This can lead to:
- Downtime and service disruptions for customers.
- Loss of revenue due to the disrupted service.
- Potentially increased costs to navigate and recover from the attack.
A not-so-fun fact: Cloudflare recently mitigated a record breaking 4.2 Tbps DDos attack that lasted for about a minute.
4. Attackers are evolving
API attacks are not static, hackers constantly try to evolve their techniques as old ones get weaker. They look for new vulnerabilities and new entry points for them to carry out their attacks.
For example, threats like Broken Object Level Authorization (BOLA) allow attackers to manipulate API requests to access data that is not meant for them. The type of attack might remain the same, but the technique used to carry out the attack will evolve over time.
A BOLA attack that you prevented today does not guarantee another successful prevention in the attacker’s next attempt. As attackers evolve their techniques, so should you evolve your API security.
5. Compliance and legal consequences
APIs handle a lot of regulated data, and failure to secure them can lead to serious financial and legal consequences. Companies operating in sectors like finance, healthcare, and e-commerce must comply with strict security regulations, including:
GDPR (General Data Protection Regulation) - requires businesses to protect personal data and notify users of breaches.
HIPAA (Health Insurance Portability and Accountability Act) - mandates secure handling of healthcare data.
CCPA (California Consumer Privacy Act) - gives consumers the right to know what data is collected and how it’s used.
Common API security threats
The OWASP API Security Top 10 list from 2023 highlights the most critical vulnerabilities that attackers commonly exploit. But before we dive into the OWASP list, let’s look at three broad types of API security threats that companies usually face:
- Making APIs unusable - Attackers overwhelm APIs with attacks like DDos
- Gaining unauthorized access - Weak authentication or authorisation flaws allow attackers to gain access that they should not have.
- Abusing business logic - Exploiting API functions in ways that can break business set API rules, leading to data theft.
These issues form the foundation of many API security risks, including those covered in the OWASP API Security Top 10 list. Now, let’s take a closer look at them:
1. Broken Object Level Authorisation (BOLA)
BOLA occurs when an API does not properly enforce authorization at the object level. This allows attackers to manipulate object IDs and access or modify data that belongs to other users.
Why does it happen:
- The API relies solely on user input without checking if the user is authorized to access the requested resource.
How to mitigate it:
- Implement strict object-level authorization checks.
- Use secure access control mechanisms to ensure users can only interact with their own data.
- Perform extensive testing to detect BOLA vulnerabilities in API endpoints.
2. Broken authentication
This vulnerability occurs when authentication mechanisms in an API are weak or misconfigured. This allows attackers to bypass login systems and gain unauthorized access.
Why does it happen:
- Weak password policies.
- Use of predictable passwords.
- API uses weak encryption keys.
How to mitigate it:
- Require re-authentication like 2 Factor Authentication for sensitive operations.
- Implement anti-brute force mechanisms.
- Do not use API keys for user authentication
3. Broken object property level authorisation
APIs often expose endpoints that return all object’s properties, particularly for REST APIs. This leads to unauthorized and unintended information exposure which can be easily used for harmful purposes.
Why does it happen:
- API responses contain sensitive object properties like user IDs and other profile details.
- Lack of strict authorization for modifying or deleting objects.
How to mitigate it:
- Implement strict property-level authorization to restrict exposure of sensitive data.
- Validate all incoming API requests to ensure users can only modify fields they are authorized to change.
- Keep returned data structures to the bare minimum.
4. Unrestricted resource consumption
APIs that do not enforce limits on requests, processing power, or storage can be exploited by attackers to overload the system, causing performance issues or service disruptions.
Why does it happen:
- No maximum allocable memory.
- No timeout system.
- No maximum upload file size.
How to mitigate it:
- Implement rate limits and throttling to prevent excessive API usage.
- Restrict the allowed file upload sizes.
- Configure spending limits for all service providers or API integrations.
5. Broken function level authorisation
APIs often expose multiple functions, some requiring a higher level of access. When these access controls are weak, attackers who do not have access can access the restricted functions.
Why does it happen:
- APIs expose high-access level functions without verifying user roles.
- Insufficient authorization checks on API endpoints.
How to mitigate it:
- Implement Role-Based Access Control (RBAC).
- Review API endpoint against function level authorization flaws.
- Enforce server-side authorisation checks for all API functions.
6. Unrestricted access to sensitive business flows
Attackers analyse the API’s business model, identify critical workflows, and automate access to these processes. This can lead to financial losses, fraud, or operational disruptions for businesses.
Why does it happen:
- APIs do not verify user intent for sensitive actions.
- No limits on the rate of API requests for critical workflows.
How to mitigate it:
- Implement rate limiting on critical API functions.
- Require user confirmation or multi-step authentication for sensitive operations.
- Monitor for unusual behavior patterns in business-critical API actions.
7. Server-side Request Forgery (SSRF)
Attackers exploit APIs that accept user-supplied URLs to send unauthorized requests. Basic SSRF is easier to exploit since the response is visible, whereas blind SSRF attacks require more guesswork but can still compromise internal systems.
Why does it happen:
- APIs allow users to define request destinations without proper validation.
- Lack of network segmentation
How to mitigate it:
- Restrict API requests to pre-approved destinations.
- Use firewall rules to block unauthorized internal network access.
- Validate user-provided URLs before making requests.
8. Security misconfiguration
Attackers look for unpatched vulnerabilities, default configurations, and exposed endpoints to gain unauthorized access. Many of these issues are well-documented, making it easier for attackers to find exploits.
Why does it happen:
- APIs expose default configurations with sensitive information.
- Weak Cross-Origin Resource Sharing (CORS) policies allow unauthorized access.
How to mitigate it:
- Regularly audit API configurations and remove unnecessary features.
- Implement secure CORS policies and disable debugging in production.
- Use automated security scans to detect misconfigurations.
9. Improper inventory management
Attackers exploit old, unpatched API versions or discover endpoints with weaker security. In some cases, exploits for outdated APIs are publicly available, or attackers gain access to sensitive data via third-party integrations.
Why does it happen:
- No centralized API inventory or version control.
- Shadow APIs (undocumented endpoints) remain unmonitored.
How to mitigate it:
- Maintain a comprehensive API inventory with all versions and endpoints.
- Regularly audit and deprecate unused or outdated APIs.
- Implement API discovery tools to detect shadow APIs.
10. Unsafe consumption of APIs
Attackers target third-party APIs that your API relies on, looking for vulnerabilities in integrations. Since this information is usually not public, it can be difficult to exploit, but once found, it can compromise the entire system.
Why does it happen:
- APIs blindly trust external responses without validation.
- Lack of sanitization for API responses.
How to mitigate it:
- Validate and sanitize all incoming data from external APIs.
- Implement zero-trust principles when interacting with third-party APIs.
- Enforce strict schema validation for API responses.
API Security best practices
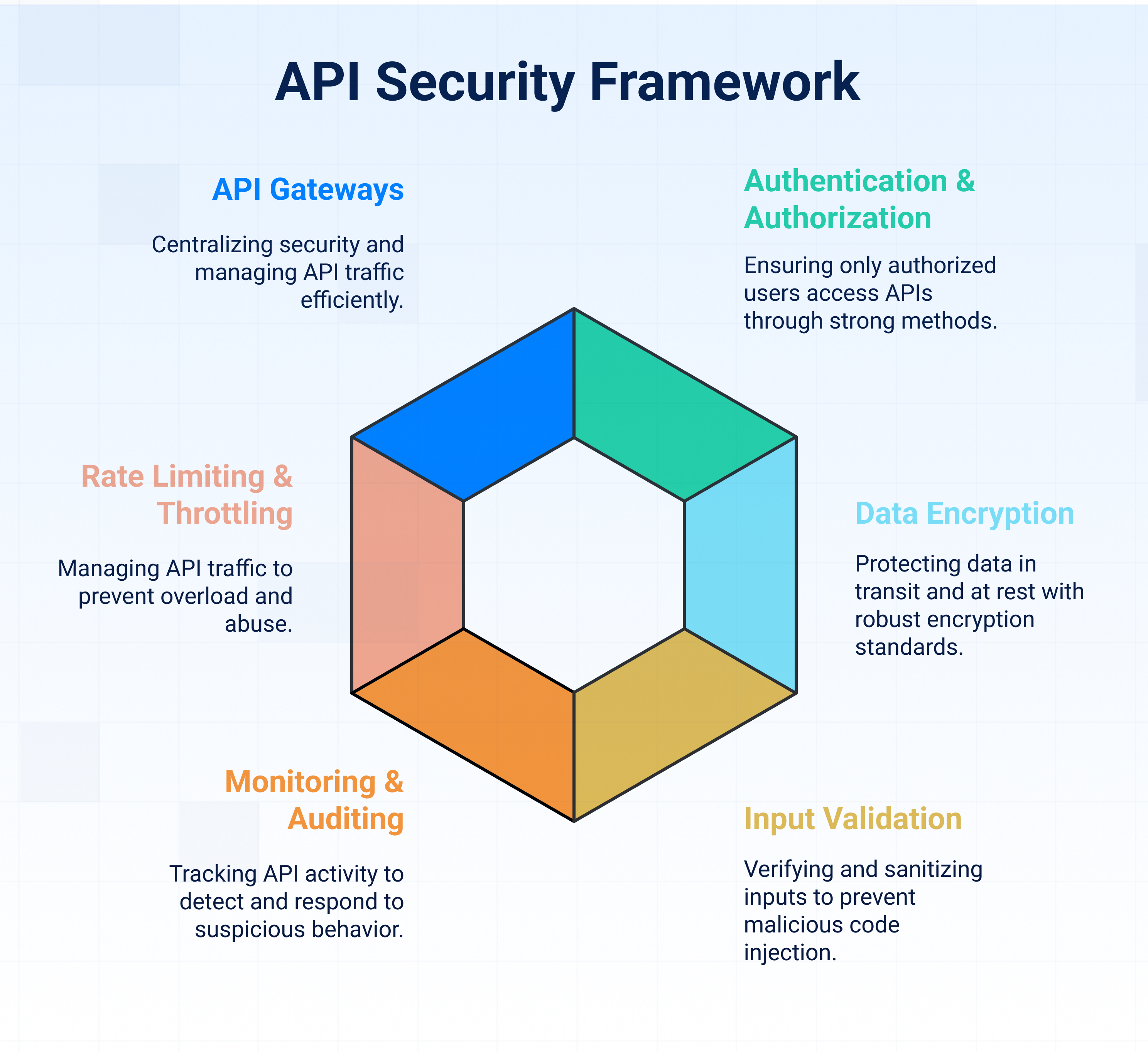
1. Use strong authentication and authorisation methods
APIs act as doors to sensitive data, so you need solid locks. Authentication ensures only the right users or systems can access your API, while authorization controls what they’re allowed to do. Standards like OAuth 2.0 and SAML Connect help keep things secure.
It’s also important to avoid using API keys as the sole authentication method as they can be easily stolen or leaked. Instead, implement token-based authentication (like JWTs) with expiration times and refresh tokens.
If possible, enable multi-factor authentication for extra security, especially for high-privilege accounts and sensitive actions.
2. Encrypt data in transit and at rest
Sensitive data is constantly moving between clients and servers, making it vulnerable to interception. Using TLS encryption (used in HTTPS protocol) protects data in transit, while encrypting stored data adds another layer of security in case of a breach.
Simply put, don’t let your API send or store anything in plain text that you wouldn’t want an attacker to see.Additionally, make sure to use strong encryption standards like AES-256 for data at rest and TLS 1.3 for data in transit and avoid outdated standards.
Regularly rotating encryption keys and storing them securely in a dedicated key management system can further reduce risk.
3. Validate and sanitize inputs
Before your API processes any input, it should check whether the data is in the expected format (validation) and remove or modify anything potentially harmful (sanitisation). This is crucial because attackers often try to inject malicious code through user inputs to exploit your API.
For example, if your API expects a number, reject anything else. This simple step helps prevent injection attacks like SQL injection and cross-site scripting (XSS). Another good practice is to use allowlists instead of blocklists to only permit specific and expected values.
4. Regularly monitor and audit APIs
Even with strong security measures, attacks can still happen. That’s why it’s crucial to log and monitor API activity to catch suspicious behaviour early.
If an API suddenly starts receiving thousands of requests from a single IP, it could be a sign of a DDoS attack. If there are multiple failed login attempts in a short period, it might be a brute force attack. By setting up real-time monitoring and alerts, security teams can respond before things escalate.
Centralised logging solutions help track API activity, while security tools can flag unusual patterns. Make sure logs are stored securely to prevent tampering.
5. Implement rate limiting and throttling
APIs can be overwhelmed by excessive requests, whether from legitimate users or attackers. This can be prevented by implementing rate limiting and API throttling. Rate limiting restricts the number of API requests a client can make in a time period, while API throttling puts excessive API requests in queues to slow things down.
For example, an API can allow only 100 requests per minute per user. If a user exceeds that, they get temporarily blocked or slowed down. This prevents abuse while keeping services available for real users. API gateway solutions provide these features for you to configure.
6. Use API gateways for centralised security
Speaking of API gateways, the number of gateways scale along with your API infrastructure. An inadequate number of API gateways can create bottlenecks, security risks, and other operational challenges.
By using multiple gateways, you improve fault tolerance, ensuring that if one gateway fails, others can keep services running. It also helps with load balancing and scalability by distributing API requests efficiently to prevent slowdowns.
API security management strategies
1. Keep Track of All Your APIs
Teams create new APIs, update old ones, and sometimes forget to retire outdated ones. These forgotten or undocumented APIs are called Shadow APIs and are prime targets for attackers because they don’t get regular security updates or monitoring.
The best way to prevent this is by keeping a complete inventory of all your APIs. This means knowing which APIs exist, who uses them, what data they handle, and how they’re secured.
Proper documentation is also a must. it helps developers and security teams understand how each API works, what permissions it requires, and where vulnerabilities might exist.
2. Adopt a zero trust security model
When it comes to API security, the old approach of “trust but verify” doesn’t cut it anymore. Zero Trust flips this idea around by assuming that no request should be trusted by default, even if it comes from inside the network. Instead, every request must be authenticated, authorized, and continuously validated.
For APIs, this means strict access controls at every level. APIs should require strong authentication (like OAuth or JWTs) and enforce least privilege access, meaning users and applications only get access to the data they truly need.
Microservices architectures especially benefit from Zero Trust, as it ensures internal API calls are secured just as tightly as external ones. By implementing continuous monitoring, identity verification, and role-based access controls (RBAC), businesses can prevent unauthorized access and limit the damage if an attacker gains entry.
3. Conduct regular security testing
APIs are constantly evolving, and with each new update, new vulnerabilities can appear. That’s why security testing should be an ongoing process, not a one-time event. Regularly scanning APIs for weaknesses helps catch issues before attackers do.
An effective way to test API security is by implementing automated vulnerability scans that help detect common issues like misconfigurations, weak authentication, and data leaks.
4. Educate and train developers on API security best practices
Even the most secure API strategy can fall apart if developers aren’t trained on security best practices. Many vulnerabilities come from simple coding mistakes like improper authentication handling, lack of input validation, or exposing sensitive data in responses.
Teaching developers how to write secure APIs is just as important as implementing security tools. A good training program should cover:
- Secure coding principles (e.g., least privilege access, data encryption, input sanitization)
- Common API security threats (like those from the OWASP API Security Top 10)
- How to use security tools effectively, such as API gateways, monitoring solutions, and testing frameworks
Encouraging security-first development practices ensures that APIs are built with protection in mind from the very start, reducing the need for costly fixes later. After all, security isn’t just a task for the security team, it’s a shared responsibility across the whole organization.
Frequently asked questions
1. Why is API security important?
APIs power everything from mobile apps to cloud services, meaning a weak API can be a direct gateway for attackers. A security breach could expose personal user data, disrupt business operations, or even result in financial losses. Strong API security ensures trust, compliance with regulations, and a smooth experience for users.
2. What are the most common API security threats?
Some of the biggest risks include stolen API keys, weak authentication, excessive data exposure, and unrestricted access to sensitive functions. Attackers can exploit these vulnerabilities to steal data, launch DDoS attacks, or manipulate business logic. That’s why APIs need multiple layers of security.
3. How can organizations improve their API security?
The best way to secure APIs is by using strong authentication (OAuth, JWT), encrypting data, setting rate limits, and monitoring API traffic for suspicious activity. Regular security testing and using API gateways with built-in protections also go a long way in keeping APIs safe from evolving threats.
You’ve spent years battling your API problem. Give us 60 minutes to show you the solution.
.svg)

%20(1).png)





.avif)
