
Internal APIs are often overlooked when it comes to security, but they can be just as risky as public-facing ones. As organisations scale, internal APIs connecting microservices, teams, and internal tools become just as vulnerable. Hardcoded tokens, over-permissive access, and network-level trust can expose sensitive data even within your own perimeter.
A zero-trust approach flips the model by assuming no user, device, or service is inherently trusted, not even inside your network. Every API call must be explicitly verified, authenticated, and authorised based on identity, context, and policy. This article breaks down what zero trust means for internal APIs, why it matters, and how to implement it without breaking your systems.
You’ll also learn step-by-step enforcement strategies, the benefits, challenges, and real-world best practices that make zero trust achievable. Whether you’re modernising legacy systems or scaling cloud-native applications, this blog will help you build a resilient, verifiable internal API ecosystem.
What is a zero-trust system in APIs?
A zero-trust system in the context of APIs is a security model that assumes no implicit trust between services, users, or devices regardless of whether they operate inside or outside the network perimeter. Instead of relying on network location or VPNs to grant access, every API request must be explicitly authenticated, authorised, and validated in real time.
In a traditional setup, internal APIs often rely on perimeter-based security: if a request comes from inside the network, it’s considered safe. Zero trust rejects this model. It treats every request as untrusted by default. Whether the request originates from a known service, a developer’s machine, or another internal microservice, it must prove its identity and permission to act.
This model is quickly becoming the norm. According to a 2025 report by StrongDM, 81% of organisations have fully or partially implemented a Zero Trust model, driven by growing internal threats and increased cloud adoption.
For APIs, this means implementing strong identity-based authentication (such as OAuth 2.0 or mutual TLS), fine-grained authorisation, continuous monitoring, and strict segmentation. Metadata like request origin, device health, and user role are used to determine access in real time. Ultimately, zero trust helps prevent lateral movement and limits the blast radius in case of a breach.
How zero trust differs from traditional API security?
.webp)
Traditional API security focuses on defending the perimeter, once inside the network, access is often assumed safe. Zero trust flips this model by treating every request as untrusted until proven otherwise. It emphasises identity, context, and continuous validation over static controls. Let’s look at the key aspects where they differ.
1. Trust model
Traditional API security assumes that anything inside the corporate network is safe. Once a service or user is past the firewall, they’re granted broad access. Zero trust, by contrast, assumes no trust by default. Every request, whether internal or external, must be verified as if it's coming from an unknown source.
2. Authentication methods
In traditional setups, static credentials like API keys or hardcoded tokens are common, often shared between services. These are easy to misuse or leak. Zero trust requires identity-aware authentication using protocols like OAuth 2.0, mTLS, or device attestation, to bind access to a verifiable entity at every call.
3. Authorisation granularity
Legacy systems often rely on coarse-grained, role-based access control. Once a role is assigned, it can perform multiple actions without additional checks. Zero trust enforces fine-grained, context-aware authorisation. Each action is evaluated in real time based on the requester’s identity, location, and intent.
4. Network dependency
Traditional models depend heavily on network-level controls, firewalls, VPNs, and IP allowlists, to block bad actors. Security is assumed if the traffic is "inside." Zero trust decouples security from network boundaries and enforces protections at the identity and application layers, regardless of the network’s origin.
5. Monitoring and response
Traditional systems often log access for auditing but rarely act in real time. Breaches may go unnoticed until it’s too late. In a zero-trust system, telemetry is constant and actionable. Requests are logged, analysed, and used to update access decisions dynamically, improving response and resilience.
6. Policy management
In older systems, access policies are usually static, manually configured, and applied across broad systems. They age quickly and are hard to adapt. Zero trust uses dynamic, automated policies that can adjust based on risk levels, context, or user behaviour, enabling real-time enforcement at scale.
Common internal API threats and vulnerabilities
While internal APIs don’t face public internet traffic, they often operate in environments where security is assumed rather than enforced. This false sense of safety leads to misconfigurations, credential misuse, and unrestricted access that attackers or even rogue insiders can exploit. Below are key threats and vulnerabilities that commonly affect internal APIs:
- Hardcoded or shared credentials: Internal APIs often rely on static tokens or shared secrets embedded in code or scripts. If compromised, these credentials can be reused silently across multiple services without triggering alerts. Despite this, only 19% of organisations rate their API defences as highly effective, and traditional security tools often fail to detect such abuses.
- Over-permissive access: APIs are frequently over-scoped, granting broader access than needed. A service meant to read data might also have write or delete permissions, increasing the blast radius in case of misuse. This excessive access contributes to the high rate of breaches and lateral movement within internal networks.
- Lack of authentication: Some internal endpoints skip authentication entirely, assuming they're safe due to being on a trusted network. This leaves them open to abuse by compromised internal machines or insider threats. Given that 53% of organisations have experienced bot attacks involving their APIs, weak authentication significantly increases risk.
- Inadequate logging and monitoring: Internal traffic is often under-monitored, with limited logging or anomaly detection. Only 21% of companies report a high ability to detect attacks at the API layer, making it difficult to spot suspicious activity or trace a breach after it occurs.
- Blind trust between services: Microservices often assume that other internal services are safe, skipping identity checks. This blind trust can be exploited to move laterally and escalate access, contributing to the multiple breach incidents many organisations face.
- Exposure via developer tools or misconfigurations: Tools like Postman collections, internal wikis, or staging environments can accidentally expose sensitive API keys or endpoints. Misconfigured CI/CD pipelines may also leak internal APIs during deployment.
- Unsecured CI/CD pipelines: APIs exposed via build, test, or deployment processes can be accessed unintentionally. Test environments often carry production-level permissions without proper safeguards.
- Stale or unused APIs: Old endpoints that are no longer maintained or documented may still be live, creating unmonitored backdoors. Attackers often target these “zombie APIs” for exploitation.
Benefits of using a zero-trust system
Zero trust is a mindset that fundamentally changes how internal systems are built and accessed. By removing assumptions of trust between services, users, and networks, it forces deliberate, verified interactions at every step. For internal APIs, this unlocks both tighter security and smarter system design. Here are seven core benefits:
1. Reduces lateral movement risk
In traditional networks, once an attacker gains a foothold, whether through phishing, credential leaks, or a vulnerable service, they can often move freely between internal APIs. Zero trust blocks this by enforcing identity and authorisation checks for every API call. Even within the network, services must prove who they are and what they’re allowed to do, sharply reducing the risk of lateral spread.
2. Minimises the blast radius of a breach
When an API key or service gets compromised, the consequences can be catastrophic if that credential offers unrestricted access. Zero trust systems implement tight, policy-driven permissions and access scopes. If a breach happens, the damage is contained to a very narrow set of actions or data, buying teams time to detect, respond, and recover.
3. Enforces least privilege across services
Most systems grant broader access than necessary, simply because it’s easier to configure. Zero trust forces a rethink, each API, user, and workload must justify exactly what access it needs. These permissions are scoped, contextual, and revocable, ensuring no entity holds more power than required for its function.
4. Enables real-time, continuous validation
In static environments, once access is granted, it often stays open until manually revoked. Zero trust introduces continuous validation of context, like who’s calling the API, what device they’re using, where they’re connecting from, and whether they’ve done anything suspicious. This makes the system adaptive and resilient to changing conditions.
5. Improves visibility and operational awareness
Zero trust requires consistent monitoring of who is calling what, when, and why. This visibility gives platform and security teams a much clearer picture of internal API usage patterns, anomalies, and access attempts. Over time, this helps fine-tune policies, detect threats early, and streamline incident response workflows.
6. Future-proof hybrid and distributed environments
With modern systems spanning cloud, on-prem, edge, and multi-region architectures, network-based controls no longer offer consistent protection. Zero trust is inherently cloud-native and platform-agnostic, it secures APIs based on identity and policy, regardless of location, helping organisations scale without sacrificing security.
7. Strengthens compliance and stakeholder confidence
Many regulatory and industry standards now include elements of zero trust, such as access audits, least privilege, and data flow controls. By adopting a zero-trust API architecture, organisations are better positioned to meet compliance requirements, reduce audit complexity, and demonstrate strong internal security practices to leadership, partners, and regulators.
Step-by-step guide to enforce a zero-trust API system
Implementing zero trust for internal APIs requires a shift in mindset as well as architecture. It’s not a one-time fix but a layered approach where identity, policy, and context drive every interaction. Here’s a structured path to get started:
- Discover and inventory all internal APIs: You cannot secure what you cannot see. Begin by identifying all your internal APIs, including those running in staging, CI/CD pipelines, and older legacy systems. Use automated discovery tools or network scanning to map endpoints, dependencies, and consumers.
- Classify APIs by sensitivity and function: Not all APIs need the same level of protection. Group them by the type of data they expose, the business function they support, and who consumes them. This helps prioritise enforcement and tailor access controls without blocking workflows.
- Remove implicit trust between services: Internal traffic is often assumed to be safe. That assumption must be removed. All services calling an API should be treated as external actors and must be authenticated explicitly. Network location or firewall rules alone should not imply trust.
- Enforce strong authentication at every hop: Use identity-aware methods like OAuth 2.0, mutual TLS, or SPIFFE to verify who or what is calling your APIs. Avoid long-lived shared secrets. Use short-lived tokens that rotate automatically and bind access to a verified identity.
- Implement fine-grained authorisation policies: Authentication proves who you are, but authorisation controls what you can do. Define access policies based on roles, attributes, and context like IP range, time of day, or device status. Use policy engines like OPA or custom RBAC/ABAC models for dynamic enforcement.
- Encrypt all internal API traffic: Even within your internal network, use TLS for all traffic. This prevents sniffing or tampering from compromised devices or misconfigured proxies. Enforce TLS at both ingress and service-to-service communication layers.
- Monitor all activity and build observability: Enable detailed logging for each request, including source, target, action, and result. Feed these logs into your SIEM or monitoring stack. Use this data to detect anomalies, audit access, and refine your trust policies over time.
- Limit access based on environment and identity: Develop policies that separate access by environment. For instance, development services should not call production APIs. Identity-based rules make it easier to enforce separation of duties and protect against accidental cross-environment access.
- Automate enforcement through gateways or service mesh: Use an API gateway, service mesh, or sidecar proxies to enforce authentication, routing, and policy centrally. This prevents teams from hardcoding security logic and makes zero trust easier to scale across environments.
- Review, rotate, and refine policies regularly: Zero trust is not a set-and-forget system. Rotate credentials frequently, decommission unused APIs, and update policies based on usage trends or detected threats. Make regular reviews part of your DevSecOps process.
Challenges while implementing a zero-trust API
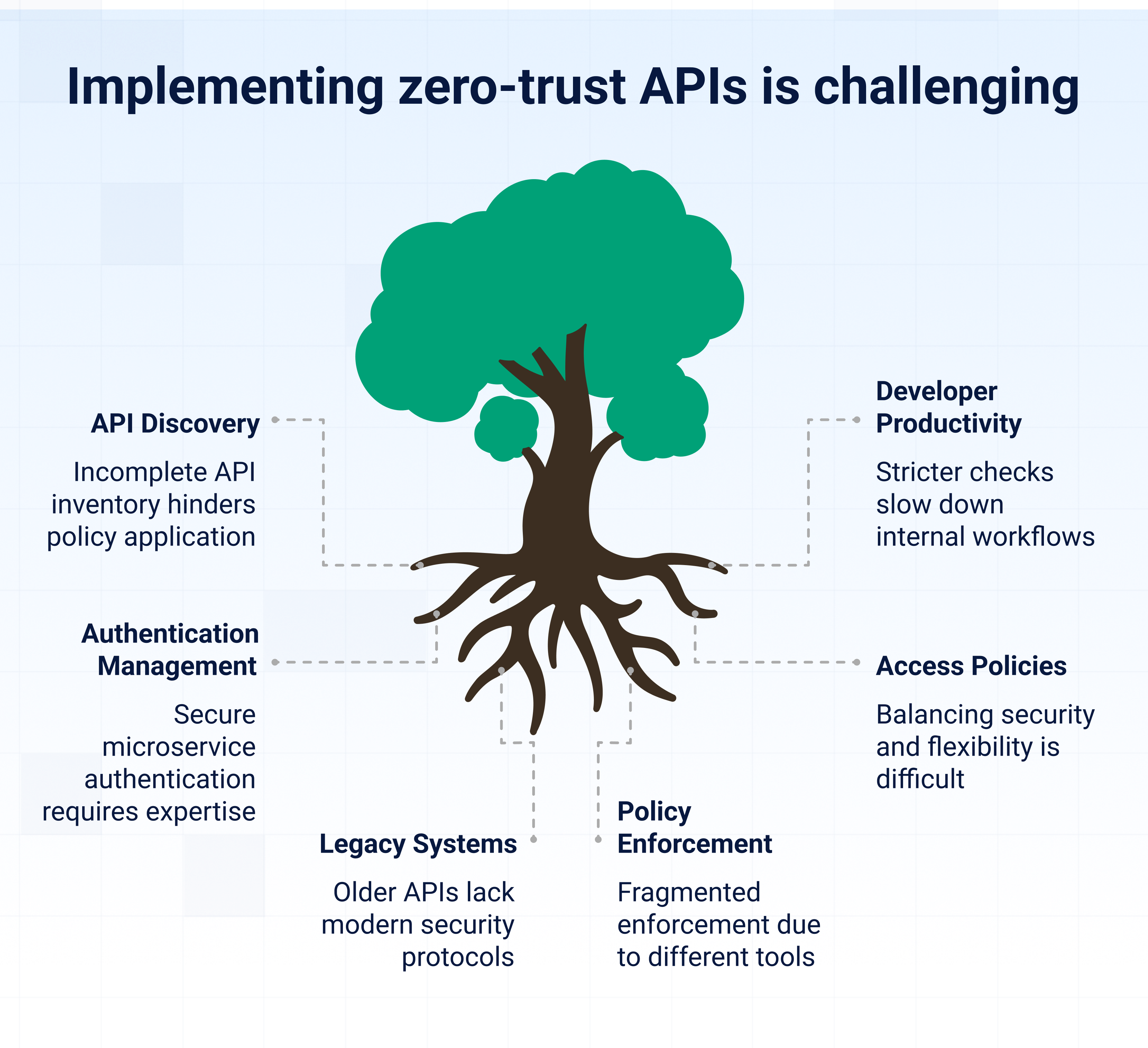
While the benefits of zero trust are clear, putting it into practice, especially for internal APIs can be complex and disruptive. It demands changes in architecture, mindset, and tooling. Here are the key challenges teams often face:
- Discovering all internal APIs: Many organisations lack a complete inventory of internal APIs, especially older or undocumented ones. Without visibility, it's hard to apply consistent trust policies or catch shadow services.
- Balancing security with developer productivity: Zero trust introduces stricter access checks, which can slow down internal workflows if not well integrated. Developers may resist added friction or face delays during debugging and testing.
- Managing service-to-service authentication: Setting up secure authentication between microservices is technically demanding. Implementing mutual TLS, SPIFFE, or identity-based tokens at scale requires expertise and infrastructure support.
- Defining fine-grained access policies: Crafting access policies that are both secure and flexible takes time. Too loose, and risks remain; too tight, and APIs become unusable. Finding the right balance is tricky.
- Dealing with legacy systems: Older APIs may not support modern authentication or encryption protocols. Upgrading or wrapping these services without breaking existing dependencies can be a major obstacle.
- Ensuring consistent policy enforcement: In large or hybrid environments, different teams may use different tools or frameworks. This leads to fragmented enforcement unless a centralised gateway or mesh is in place.
- Scaling monitoring and observability: Zero trust depends on real-time insights into API usage and behaviour. Setting up the infrastructure to log, analyze, and alert on every internal request can be resource-intensive and noisy if not tuned properly.
Best practices for zero-trust API security implementation
Zero-trust for APIs goes beyond authentication and encryption. It's about rethinking how services trust one another, how credentials are handled, and how decisions are logged and enforced. These best practices help build a system that's not only secure but maintainable at scale.
1. Make API identity a first-class citizen
Just as users have unique identities, every API or microservice should too. Assign cryptographic identities using certificates or service identities like SPIFFE to ensure that trust decisions are always based on verifiable sources. This enables precise authentication and removes reliance on IPs or network zones.
2. Design APIs to fail closed, not open
Many systems default to permissive behaviour when things go wrong, like skipping authentication if a token service is down. In zero trust, APIs must deny all requests by default and require all checks to pass before granting access. This prevents fallback paths from becoming vulnerabilities.
3. Shift trust validation to the edge
Where you validate trust matters. Enforce identity, authentication, and authorisation as early in the request flow as possible, ideally at the API gateway, mesh proxy, or edge layer. This limits the exposure of backend systems and reduces the cost of processing invalid or malicious requests.
4. Rotate credentials and secrets frequently
Stale tokens and long-lived secrets are a liability. Implement automation to issue short-lived, scoped credentials that expire quickly and rotate often. This way, even if a credential is leaked, its usefulness is limited and recovery doesn’t require emergency rewrites or mass revocation.
5. Segment APIs by business or risk domain
Don’t treat all APIs equally. Organise them into domains, such as finance, HR, or internal tools, and apply different trust policies to each. If one domain is compromised, domain segmentation ensures that others remain isolated and protected from lateral movement.
6. Log and audit trust decisions, not just access
Most systems log requests, but in zero trust, you also need to capture why access was granted. Include which policy was evaluated, which identity was verified, and under what conditions the request was approved. This gives your team a full picture for audits, forensics, and refinement.
FAQs
1. Can you implement zero trust without a service mesh?
Yes, zero trust can be implemented without a service mesh by using API gateways, identity-aware proxies, and strict access controls. However, service meshes simplify enforcement by handling mTLS, traffic policies, and observability at scale. For microservice-heavy architectures, a mesh makes zero trust more manageable but isn’t strictly required.
2. How does mTLS help enforce zero trust for APIs?
Mutual TLS (mTLS) ensures that both the client and server authenticate each other during every API call. This mutual verification enforces strict identity checks, prevents spoofing, and encrypts traffic. In a zero-trust model, mTLS helps ensure no service is trusted implicitly, even inside the internal network.
3. Is OAuth 2.0 enough for zero-trust API security?
OAuth 2.0 provides strong user and application-level authentication and scoped access, making it a key building block for zero trust. However, it isn’t sufficient on its own. Zero trust also requires continuous authorization, identity-bound tokens, network segmentation, and contextual policies to fully secure internal APIs.
4. Do internal APIs need authentication in a zero-trust model?
Yes, authentication is mandatory for all internal APIs in a zero-trust system. Even if the traffic originates from within the network, it must be explicitly verified. This prevents unauthorized access from compromised services or insiders and ensures every call is made by a known, authenticated identity.
5. What’s the difference between zero trust and API gateways?
API gateways manage traffic routing, rate limiting, and protocol translation. Zero trust is a security framework focused on identity, policy, and verification. While gateways can help enforce zero trust, the concept extends beyond tooling—it requires continuous validation of every request, regardless of location or network trust.
You’ve spent years battling your API problem. Give us 60 minutes to show you the solution.
.svg)

%20(1).png)





.avif)
