.png)
APIs are everywhere. Too many, in fact. Some are tracked. Many are forgotten. And the forgotten ones, the shadow APIs, are where breaches begin.
By 2026, APIs will power more than 80% of web traffic. Yet most enterprises can’t even list all of theirs. It’s because manual inventories buckle under sprawl. Developers move on to new projects, leaving old endpoints undocumented. Security teams try to stitch together visibility from incomplete logs and scattered tools. And in the gaps, attackers look for the one API you didn’t know existed.
That’s why API discovery platforms exist. They shine light on these hidden gaps, turning API chaos into a clean inventory and blind spots into actionable insights.
This blog is your field guide, walking you through the ten best API discovery platforms to trust in 2025, and how to pick the right one for your team.
Because here’s the truth, you can’t protect what you can’t see.
So let’s get started:
What is API discovery?
API discovery is the process of finding and cataloging every API in your environment, whether they are formally documented or not. It answers a simple but critical question: what APIs do we actually have?
The challenge is that most organizations can’t answer that with confidence. APIs are created in sprints, integrated into apps, and left behind as teams move on. Some are documented. Many aren’t. Over time, this creates a shadow layer of endpoints that no one tracks but still live in production.
These “shadow APIs” and their cousins, “zombie APIs” (old versions left running), pose serious risks. They may not follow current security standards. They may expose sensitive data. And because they’re invisible to inventory, they’re often missed by monitoring and testing.
Why API discovery matters?
API discovery matters because you can’t protect, govern, or scale what you can’t see. Without it, organizations face hidden security risks, compliance failures, and mounting costs from unmanaged endpoints.
Enterprises now run hundreds or thousands of APIs across microservices, multiple clouds, and legacy systems. New APIs are deployed constantly, while old ones linger in production. Visibility vanishes fast, and the manual approach of relying on spreadsheets breaks down under modern scale.
That’s why automated API discovery has become essential. Platforms can scan traffic, code repositories, gateways, and logs to detect APIs in real time. Instead of chasing ghosts, teams get a living map of every endpoint.
In short, API discovery is visibility. And visibility is the foundation of security, compliance, and governance in an API-driven world.
Key features to look for in API discovery platforms
Not all API discovery tools are created equal. Some give you a flat list of endpoints and stop there. The problem? A raw list doesn’t tell you which APIs are active, who owns them, what data they expose, or how they connect to other systems. Without that context, you still don’t know where the risks or dependencies lie.
The best platforms go further, mapping usage, ownership, and security posture in real time.
Choosing the right one means knowing which features separate the essentials from the noise.
Here are the features that matter, and why:
1. Automated discovery: Manual tracking fails at scale. Automated discovery continuously scans network traffic, gateways, and code to uncover every API, including the ones no one documented.
2. Version tracking and change detection: APIs evolve. Silent changes can create vulnerabilities or break dependencies. Version tracking ensures every modification is logged, flagged, and understood before it becomes a problem.
3. Comprehensive API inventory: A searchable catalog turns chaos into clarity. It gives DevOps, security, and compliance teams a single source of truth for every API, past and present.
4, Usage analytics and monitoring: Visibility isn’t just about what exists; it’s about how it’s used. Analytics reveal adoption, usage spikes, and anomalies that may indicate abuse or misconfiguration.
5. Dependency mapping: APIs rarely stand alone. Dependency mapping shows how services connect, so teams can predict the ripple effects of downtime, changes, or attacks.
6. Security risk assessment: Discovery without a security context is half the story. Risk assessment flags weak authentication, exposed sensitive data, or endpoints violating the OWASP API Security Top 10.
7. Integration with API management tools: Discovery is most powerful when it plugs into gateways, CI/CD pipelines, and security platforms. Integration ensures new APIs are caught early and policies are applied consistently.
Top 10 best API discovery platforms in 20256
1. DigitalAPI - API discovery platforms
Enterprises don’t just have too many APIs, but they have too many gateways. Different teams adopt different platforms, each with its own catalog and way of working. The result? APIs are scattered across silos, impossible to track, harder to reuse, and often forgotten.

This fragmentation kills visibility. Developers waste time rebuilding what already exists. Security teams miss shadow endpoints hidden behind different gateways. Compliance officers can’t produce a clean inventory. And leadership? They get a sprawl of APIs with no clear owner, no adoption, and no ROI.
DigitalAPI.ai fixes this by creating a single plane of visibility across all your gateways. Every API, regardless of where it lives, gets cataloged into one unified, searchable hub. No blind spots. No duplication. Just clarity.
- Unified catalog across gateways: DigitalAPI brings all your APIs onto one, searchable hub. This helps your teams move faster as it eliminates any silos, minimizes redundant APIs and work, and drives better adoption.
- End-to-end lifecycle management: It doesn’t just stop at discovering and cataloging, but DigitalAPI also helps you manage them throughout their lifecycle, reducing compliance and governance burden. It covers the entire lifecycle stages like documentation, governance, monitoring, and retirement.
- AI assistance at every step: Automates OWASP checks, duplicate detection, documentation, testing, and workflow management.
Instead of fragmented lists across gateways, you get one central source of truth. That visibility drives discovery. Discovery drives adoption. And adoption drives value.
2. Salt Security
Salt Security offers runtime-first discovery, turning live traffic into a detailed API inventory enriched with behavioral analytics.
Here’s what you can expect with Salt Security’s API Discovery platform:
- Traffic-driven discovery: It can find known, shadow, and zombie APIs with out-of-band analysis.
- Cloud Connect for AWS: It enables agentless cloud-native discovery, allowing you to just plug it in and be ready to go.
- Works with major cloud services: The tool is aligned with major API gateways and cloud services, making it readily deployable into your infrastructure.
- Secure from the ground up: The tools are developed with security in mind. This means that it can help with runtime analytics and even governance when paired with catalog tools.
Salt is an option for enterprises with sprawling, fast-changing estates that need visibility and real-time risk context.
3. Traceable AI
Traceable AI turns discovery into long-term analytics by feeding all findings into an API Data Lake, bringing you more comprehensive API context like dependencies, where they are hosted, and what services are accessing them. That context helps teams prioritize risks, understand potential blast radius, and strengthen overall posture.

Here are some USP of Traceable AI
- Multi-source discovery: it can discover APIs from multiple channels like traffic, gateways, code, and even eBPF workload hooks, reducing your overhead.
- Monitoring as per set SLAs: The tools come with capabilities to monitor, track, and flag drifts over time and reveal any undocumented endpoints.
- Helps maintain posture: The Analytics layer makes it ideal for investigations, trend analysis, and posture management.
- Broad coverage requires thoughtful integration: The platform shines when data sources are fully connected.
- Borader API context: It maps dependencies, hosting locations, and access patterns, giving security and ops teams a 360° view of how APIs interact in real environments.
Traceable is a strong choice if you want discovery plus analytics depth to guide both security and compliance.
4. Akamai API Security
Akamai’s API Security, strengthened by its 2024 acquisition of Noname, works for enterprises running at the edge.
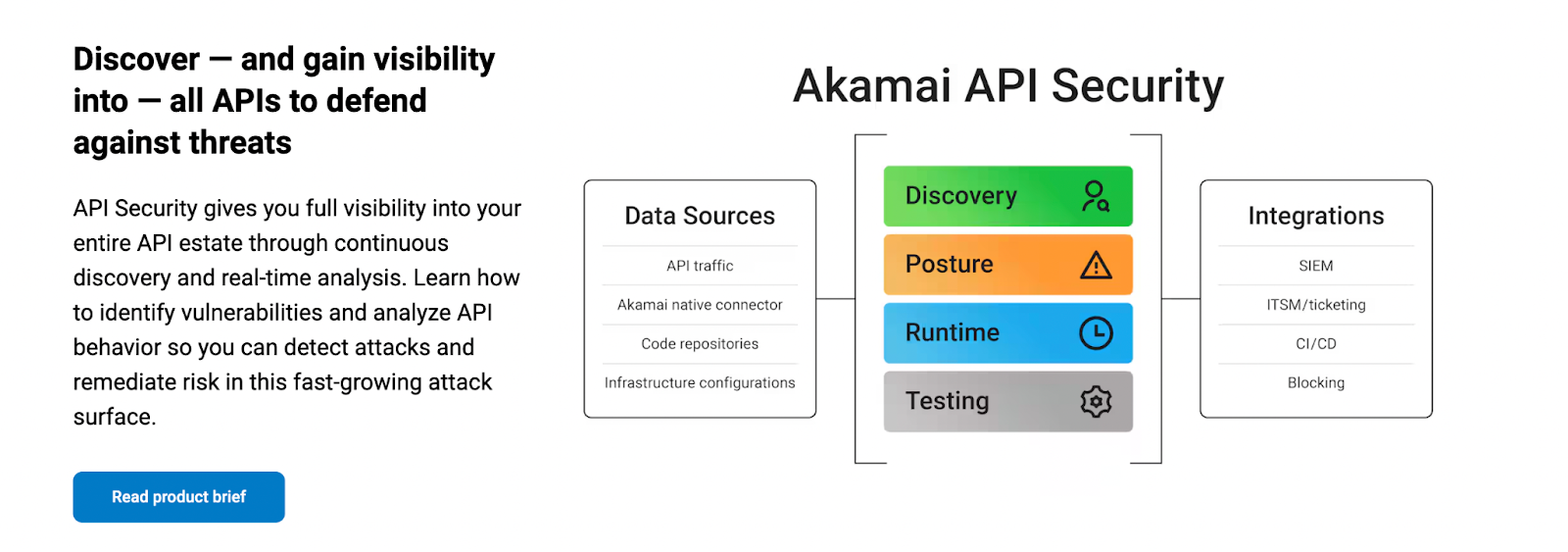
Here’s what this tool can offer.
- Continuous, traffic-based discovery of shadow, zombie, and rogue APIs.
- Pairs discovery with classification and runtime protections.
- Tight integration with WAAP, bot defense, and DDoS solutions.
- Best for organizations standardizing on Akamai’s security stack.
For enterprises already on Akamai, this is the logical way to unify API discovery and protection.
5. Cequence Security
Cequence offers a dual lens: attacker’s view (outside-in) and internal view (inside-out), merging both into a unified inventory.
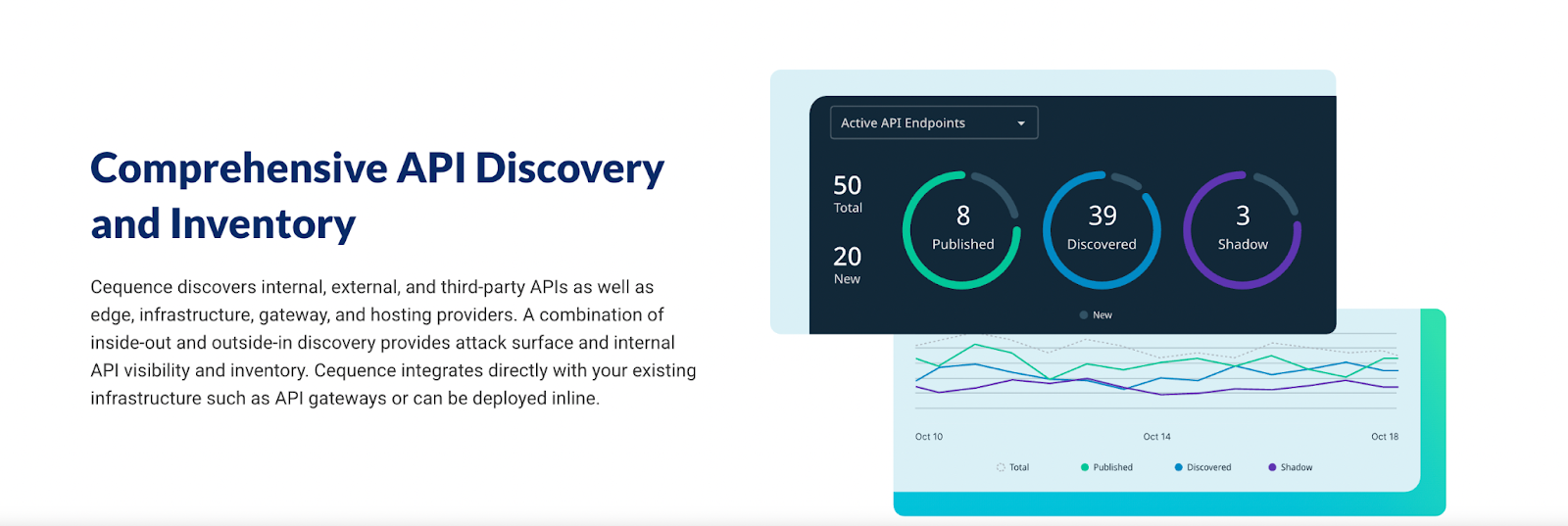
- External mapping surfaces public APIs you may not know are exposed.
- Internal integrations and sensors cover private APIs.
- Lightweight to deploy and doesn’t require deep instrumentation.
- Outside-in findings are invaluable, though still complemented by internal scanning.
Cequence is ideal for organizations that want comprehensive visibility and API discovery capabilities without sacrificing internal accuracy.
6. Imperva API Security
Imperva blends continuous discovery with automated risk classification.

- Uncovers shadow APIs and tracks changes across environments.
- Flags design flaws and OWASP API Top 10 vulnerabilities.
- Built-in classification helps prioritize sensitive endpoints.
- Best integrated with Imperva’s broader WAF and bot protection stack.
- Imperva also defends against issues like BOLA (unauthorized access to data) and BOFLA (unauthorized use of functions) by monitoring behavior, spotting abnormal requests, and enforcing correct authorization flows.
Imperva is a good fit if you want a straightforward “discover + classify” workflow that feeds directly into governance and protection.
7. Palo Alto Networks Prisma Cloud
Prisma Cloud makes API discovery a native feature of cloud security posture management.

- Discovers APIs across cloud workloads and services.
- Maps risks in context with exposures, vulnerabilities, and identities.
- Provides attack-path views to prioritize what to fix first.
- Strongest for cloud-first environments; validate fit if most APIs are on-prem.
Prisma is best for teams already using Palo Alto’s CNAPP stack and wanting API discovery tightly woven into cloud risk management.
8. Microsoft Defender for APIs
For organizations running on Azure, Defender for APIs offers low-friction discovery and monitoring.

- Continuous discovery across Azure API Management, Logic Apps, and Function Apps.
- Surfaces unified inventory, recommendations, and real-time alerts.
- Integrates seamlessly with Defender for Cloud and SIEM tooling.
- Onboarding can add load to APIM; Microsoft advises a gradual rollout.
If you’re invested in Azure, Defender for APIs is the natural extension of your cloud security workflow.
9. Google Apigee
Apigee combines API Hub for cataloging with Shadow API Discovery for finding the undocumented.
- Observation jobs, or automated tasks, analyze traffic for shadow APIs and reconcile the information anomaly detection.
- Centralizes shadow discovery results into API Hub.
- Includes anomaly and abuse detection through Advanced API Security.
- Powerful AI support helps manage the lifecycle of APIs and make their discovery more accurate and efficient.
Apigee can be a good choice for Google Cloud customers who want catalog a
10. Postman
Postman brings discovery into the developer workflow through its new Insights feature.

- Postman Insights Agent observes traffic and automatically surfaces endpoints per service.
- Endpoints view lets teams validate, merge, and refine discovered endpoints, improving accuracy while keeping humans in the loop.
- Integrates with Postman’s Private API Network for cataloging and reuse.
- Discovery connects seamlessly with testing, monitoring, mocking, and documentation features that developers already rely on.
Postman is ideal if you want discovery embedded in the software development lifecycle, keeping developers in the tools they already use.
How to choose the right API Discovery software?
Selecting an API discovery platform isn’t a minor technical choice, but it’s a strategic decision that affects security posture, compliance readiness, developer velocity, and cost control. The stakes are high; the wrong tool leaves blind spots, creates operational drag, and adds expense without solving the underlying problem.
The following factors cut through the noise and help align the right API discovery tool to your organization’s needs:
1. Scalability & coverage
As your number of services, microservices, and cloud functions grows, the discovery tool must be able to handle volume, integrate with multiple hybrid or multi-cloud environments, and handle spikes in traffic without lag or blind spots.
You need to know if:
- Does the tool process traffic, logs, and code smoothly?
- Can it discover dormant or rarely-used APIs?
- Can it scale across regions or clouds?
2, Accuracy & False Positive Control
Once you have triaged a platform on its scalability, you need to see if the platform is reliable and accurate in the insights and API it reveals. Because a flood of false alarms can waste your security/dev teams’ time, false negatives can mean missing endpoints, leaving your security posture vulnerable.
You’d need to ask if:
- Does the tool distinguish real APIs from non-API endpoints?
- It categorizes endpoints by risk (authentication, data sensitivity)?
- Is the tool reliable with discoveries when usage is intermittent?
3. Compliance & regulatory fit
When APIs handling sensitive data go undocumented, compliance teams lose the ability to prove controls, document exposure, or pass audits. A strong discovery platform closes that gap by surfacing the endpoints that matter and producing evidence that regulators will expect.
If you’re in regulated verticals (health, finance, etc.), you’ll need audit trails, documentation, data residency, and privacy standards.
That’s why it’s important to evaluate whether an API discovery tool can:
- Classify sensitive data such as PII, PHI, or financial information flowing through APIs.
- Highlight exposure levels and flag endpoints that may violate compliance standards.
- Produce audit-ready logs and reports that satisfy regulators and internal governance teams.
- Map findings to established frameworks like GDPR, HIPAA, or PSD2 to streamline audits and reduce manual effort.
4. Integrations & ecosystem compatibility
API discovery doesn’t happen in isolation. The tool must connect to gateways, CI/CD, logs, API management, security tools, and monitoring dashboards. If the tools' integration capabilities are weak, you get silos and duplicated effort. Worse, it may not connect to your entire tech stack altogether, leaving gaps in API discovery.
When evaluating, push beyond sticker price and ask:
- Does the version of the tool fit your growth trajectory (subscription vs usage vs tiered)?
- Are there overage fees if traffic or endpoints spike?
- Does the tool require extra infrastructure, agents, or cloud resources?
- What training or tuning will your team need—and how much time will that take?
- How much does enterprise-grade support cost, and is it bundled or extra?
The goal isn’t to buy the cheapest tool. It’s to understand the true, long-term cost of ownership—and ensure the value matches the spend.
5. Cost & total cost of ownership (TCO)
The pricing you see on the website doesn’t always translate to the actual cost. It depends on how you use the software.
Price per API call, per request, per endpoint, number of environments, and support plans vary wildly. There might also be some hidden costs, like virtually mandatory onboarding, custom integrations to fit the product into your existing stack, and time you’d need to train your teams on it.
You need to evaluate a tool for:
- Pricing model (subscription vs usage vs tiered)
- Overage fees
- Infrastructure or agent requirements
- Costs of training and tuning, ongoing maintenance, and support tiers.
6. Use-Case Alignment
Not every team has the same priority. If your top concern is catching shadow APIs and making your system more resilient, you need discovery that’s aligned with security (traffic, risk scoring).
But if your priority is enabling developers, you want tools with catalogs, metadata, and ease of use. And if all you need is inventory, a simpler tool with basic discovery capabilities may suffice.
Depending on your use case, you need to evaluate the tools based on:
- If the tool support multiple discovery modes (code, traffic, logs)?
- How good is its developer UX, and how easy is it to maintain catalogs, ownerships, and metadata?
- If the tool allows roles/permissions for security vs dev teams?
7. Support, visibility & reporting
API discovery is useful only if the insights are contextual. This means that you get more than just an inventory but also visibility into risks, metadata, and ownerships, so it can inform your decisions to uphold security practices and compliance.
Beyond that, you need a vendor for support and SLAs besides the feature. Because when issues like integration hiccups, false negatives, and reporting glitches arise, you need assurance that the vendor can respond quickly.
Why DigitalAPI.ai is the platform you need
If you’ve spent time managing APIs, you know the drill.
You run a discovery tool, and it surfaces mostly what you need to see. Shadow APIs, duplicates, and vulnerable endpoints.
But discovery only shows you the gaps you need to fix. It doesn’t help you clean it up, govern it, or make it actionable for developers right away.
That’s the gap a consolidated platform like DigitalAPI.ai fills. It builds on discovery and gives you the missing piece — a way to organize, secure, and scale APIs so they become assets, not liabilities.
Here’s why you need it:
- It unifies everything: DigitalAPI.ai pulls in APIs from across all your gateways and services. It automatically detects duplicates, enriches them with metadata, and generates documentation. The result is saved bandwidth. It brings you the entire inventory in a searchable, developer-friendly format that actually helps them find, manage, retire, or reuse APIs.
- Makes you compliant from the ground up: Instead of chasing down rogue endpoints, you get guardrails built in. Policies are enforced automatically, OWASP checks run without manual setup, and APIs stay consistent across teams. With DigitalAPI, governance isn’t an afterthought, but it gets baked into the workflow.
- AI That Turns API Chaos Into Control: Teams drown in manual reviews, inconsistent standards, and endless firefighting just to keep services reliable and secure. DigitalAPI uses AI to eliminate that grind. From automated compliance checks and contract validation to OWASP security scanning, workflow automation, and real-time anomaly detection, it does the heavy lifting. So your teams finally get to focus on scaling, innovating, and delivering business outcomes.
- End-to-end lifecycle management: From the design stage to discovery, governance, monitoring, and monetization, DigitalAPI covers the entire lifecycle. You don’t need to stitch together half a dozen tools, but it provides one layer of control across the board.
Challenges and limitations of an API discovery platform
While API discovery platforms offer more visibility and control, they also come with their own sets of challenges. For example, when these tools flag benign or non-vulnerable APIs as threats, they bottleneck teams and divert their focus to insignificant tasks, draining time, resources, and costs.
Thus, decision makers need to understand these shortcomings to set their expectations and plan around them, turning potential stumbling blocks into manageable considerations.
- False Positives in automated scanning: Most API discovery tools analyze traffic, logs, and code to automatically identify vulnerabilities. But it's not always reliable. Sometimes they flag non-API endpoints or bring up duplicate results that add to the noise. Teams get distracted and drain bandwidth chasing and fixing the wrong gaps.
- Integration Overhead: Discovery platforms rarely operate in isolation; they need to plug into gateways, CI/CD pipelines, cloud providers, and monitoring tools. Setting up these integrations can require time, custom work, and coordination across multiple teams.
- Cost of Enterprise-Grade Solutions: Advanced discovery platforms come with enterprise pricing models. Licensing fees, usage charges, infrastructure requirements, and premium support plans add up quickly. Without a clear ROI, costs can outweigh benefits. Careful evaluation of the total cost of ownership is essential before scaling.
- Skill Requirements to Operationalize Insights: Discovery generates data, but data alone doesn’t solve problems. Teams still need the skills to interpret findings, connect them to governance and security workflows, and act on risks.
FAQ
1. What is the difference between API discovery and API management?
While API discovery only refers to the process of finding APIs and endpoints to maintain a comprehensive inventory, API management refers to managing APIs throughout their lifecycle. This means that while API discovery ends at revealing all undocumented, shadow, and internal APIs, API management goes all the way from publishing to defining policies, monitoring usage, upgrading, and retiring them.
2. How do API discovery tools detect shadow APIs?
Different API discovery tools deploy a combination of different techniques to reliably discover shadow APIs in the network. These techniques include analyzing network and gateway traffic, monitoring logs, endpoint probing and fuzzing, and codebase and system scanning. Some tools also use AI and machine learning to analyze large codebases or huge volumes of traffic to efficiently discover APIs with accuracy.
3. Are API discovery platforms necessary for small businesses?
Yes, API discovery platforms are necessary for businesses of all sizes because even a few hidden or shadow API can compromise the security or compliance posture. For small businesses, a full-blown enterprise suite might not be needed, but at least a lightweight discovery tool would be necessary.
4. What role does AI play in API discovery?
AI can make API discovery more efficient and accurate. It can analyze large volumes of traffic, logs, and usage patterns to detect anomalies and uncover hidden or shadow APIs more accurately. It can also analyze the payload to clearly categorize endpoints. For example, it classifies which endpoints handle PII and which ones handle PHI, which simplifies compliance.
5. Can API discovery help with regulatory compliance?
Yes, an API discovery tool can take a lot of the pain out of staying compliant. It handles the manual, grunt work like keeping track of what data’s being used, where it’s going, and who’s accessing it. It also leaves an audit trail so you can actually prove you're doing things by the book. That makes it way easier to stay on the right side of rules like GDPR, HIPAA, PSD2, and SOC 2.
You’ve spent years battling your API problem. Give us 60 minutes to show you the solution.
.svg)

%20(1).png)



.avif)
