Blog
API Dev Portal for Better RBAC: Secure, Manage, and Scale Access Control
Updated on:
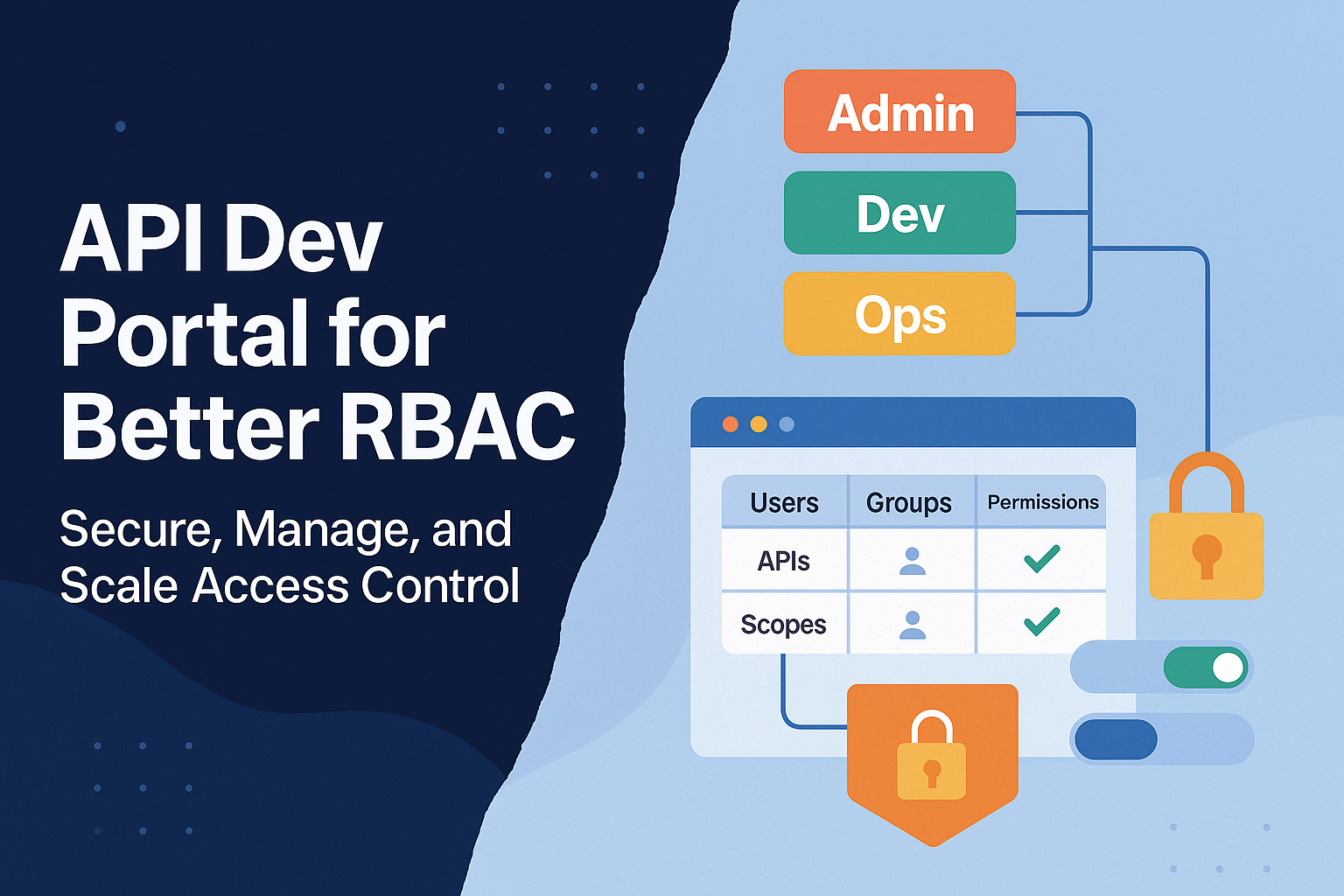
Implementing Role-Based Access Control (RBAC) in your API Developer Portal is key to securing sensitive data and managing access efficiently. RBAC assigns permissions based on roles like admin, developer, or partner rather than individual users, reducing the risk of unauthorized access.
Defining clear roles and aligning permissions with business rules ensures internal developers have full access while external developers see only what they need. This supports compliance, governance, and a smooth workflow across teams.
DigitalAPI enables secure, scalable API Developer Portals with integrated RBAC. Its AI-powered management tools simplify access control, enhance security, and improve the overall developer experience.
See it in action!Book a demo today to explore
What happens when anyone in your organization can access everything in your API Developer Portal?
The portal is where teams discover, test, and manage APIs. But without proper API developer portal role-based access control, you will end up with chaos, such as developers accessing sensitive endpoints, partners overstepping permissions, and admins drowning in manual approvals.
This will lead to security gaps, compliance risks, and stalled innovation. And you know what? Apart from slowing down workflows, poorly managed API dev portal user roles and permissions open doors to breaches and erode trust across your API marketplace.
But do you need to lock everything down? Not necessarily, you need to follow API dev portal security best practices that ensure smarter access.
This blog will teach you how to manage your API dev portal for better RBAC. Let’s explore how to make it work.
What is RBAC in an API developer portal?
Role-based access control in an API developer portal is a security mechanism that manages user access based on predefined roles and responsibilities.
Instead of granting unrestricted permissions to every user, the API developer portal role-based access control assigns privileges according to roles such as admin, developer, or partner.
This structured model helps ensure secure API developer portal access by limiting exposure only to the resources a user truly needs.
RBAC is important in an API developer portal for the following reasons:
- Enhanced security: A key part of API dev portal security best practices, RBAC prevents unauthorized access by restricting sensitive APIs and data.
- Simplified management: With API dev portal user roles and permissions, administrators can assign access consistently without managing individuals.
- Scalability: As organizations grow, an API dev portal ensures role assignments scale efficiently across larger developer communities.
- Compliance: RBAC supports regulatory requirements by enforcing structured permissions and maintaining secure access logs.
What are the key components of RBAC in API dev portals?
The core components of a role-based access control system in the API developer portal include:
- Users: In an API developer portal role-based access control system, users are individual developers, admins, or partners who require access to the portal. They represent the entities whose identities are authenticated and whose actions are governed by enterprise RBAC for developer portal policies.
- Roles: Roles define the grouping of access levels within the portal, such as “API consumer,” “API publisher,” or “portal admin.” They simplify secure API developer portal access by assigning privileges collectively instead of managing each user individually.
- Permissions: Permissions specify what actions are allowed based on assigned roles. For instance, a consumer may have permission to view documentation, while an admin can modify APIs.
- Resources (Objects): Resources are the protected assets within the API developer portal role-based access control framework, such as API documentation, test environments, or usage analytics dashboards. Controlling access to these ensures enterprise-grade security and proper segregation of responsibilities.
- Operations: Operations define the specific actions that can be performed on resources, like read, write, update, or delete. These actions enforce secure API developer portal access by ensuring users only interact with objects according to their role-based permissions.
How to plan RBAC for your API developer portal step by step
To implement role-based access control (RBAC) in your API dev portal for better RBAC, assess API security requirements, map out user roles, align permissions with business rules, and then build a role hierarchy to structure roles and avoid permission overlaps.
Let’s break down each step in detail:
1. Assess API security requirements
Before setting up the API developer portal role-based access control, evaluate security needs. Identify which APIs handle sensitive data, require authentication, or must comply with regulations like GDPR or HIPAA.
Conduct a risk assessment to determine access tiers for public, internal, or partner-only. This ensures your API dev portal security best practices align with organizational policies.
2. Map out user roles
From there, define distinct roles such as:
- Internal developers – Full access to internal APIs.
- External developers – Limited access to public APIs.
- Partners – Custom access to shared integrations.
- Admins – Full control over the portal.
Mapping out user roles prevents unauthorized access and simplifies API dev portal permissions management.
3. Align permissions with business rules
Then assign permissions based on job functions. For example, partners may only need read access, while admins require edit/delete rights.
Use policy templates to standardize permissions and enforce least-privilege access for a secure API developer portal access model.
4. Build a role hierarchy
Lastly, design a hierarchical structure where higher roles inherit lower-level permissions. For instance, an admin inherits developer rights, reducing redundancy. Avoid giving excess permissions by regularly auditing roles.
How to implement RBAC in your API dev portal the right way
To implement RBAC in your API dev portal correctly, you need to focus on choosing the right API gateway and management platform, integrating identity providers, creating clear role assignment workflows, and enforcing permissions with strict policies.
Let’s explore the steps further:
1. Choose the right API gateway and management platform
The foundation of enterprise RBAC for developer portal success lies in selecting the right API gateway and management platform. A robust gateway allows you to define, enforce, and monitor API dev portal user roles and permissions efficiently.
DigitalAPI is a strong choice here. With its advanced role management, API lifecycle support, and built-in security tools, it helps organizations implement secure API developer portal access seamlessly. Explore DigitalAPI to simplify RBAC in your API dev portal.
2. Integrate identity providers (SSO, OAuth, OpenID)
A key strategy for secure access is connecting the portal with trusted identity providers. Using standards such as Single Sign-On (SSO), OAuth, and OpenID ensures that authentication and authorization are unified across systems.
This minimizes risks, eliminates password fatigue, and ensures role mapping aligns with organizational policies for API dev portal security best practices.
3. Create role assignment workflows
To ensure consistency and avoid privilege creep, define structured workflows for assigning user roles.
For instance, developers may need read-only access to documentation, while admins require configuration rights. Using automated workflows tied to HR or IT systems can streamline onboarding and maintain compliance for enterprise RBAC for developer portal environments.
4. Enforce permissions (middleware, API policies)
Finally, remember to enforce permissions through middleware and API policies. This means validating every request against user roles, preventing unauthorized data access, and ensuring secure API developer portal access at all levels.
You can use dynamic policies to allow administrators to adjust access as business needs evolve.
Best practices for managing RBAC in API dev portals
Managing role-based access control (RBAC) within an API developer portal is critical to give users the right level of access without exposing sensitive resources.
You can use a well-structured RBAC approach to balance security with usability, which gives developers and stakeholders the access they need while maintaining strong safeguards.
Below are some best practices to guide you in implementing and maintaining RBAC in your API dev portal.
1. Define clear roles and permissions
The foundation of the API developer portal role-based access control lies in having clearly defined user roles. Instead of assigning access on an ad hoc basis, outline a consistent structure such as admin, developer, partner, or read-only user.
Each role should come with well-documented permissions that dictate exactly what actions they can perform, from viewing API documentation to managing keys.
For example:
- Developers may need API key management and documentation access.
- Admins require full control, including user management and analytics.
- Partners might only need limited API access.
This clarity reduces confusion, prevents privilege creep, and makes onboarding new users more straightforward.
2. Implement a robust authorization system
Once roles and permissions are established, the next step is ensuring your portal enforces them reliably. This means adopting an authorization system that can validate requests in real time and prevent unauthorized activity. Strong API dev portal permissions management ensures that only the right people can create, update, or delete resources. Leveraging standards like OAuth 2.0 or JWT tokens can strengthen trust while also allowing flexibility for future integrations.
3. Streamline role assignment and management
RBAC should not create unnecessary administrative overhead. Automating role assignment, perhaps through integration with identity providers or single sign-on (SSO) platforms, helps streamline the process.
This prevents bottlenecks and ensures users are quickly provisioned with the correct API dev portal user roles and permissions. Regular reviews of assignments are also key to making sure former employees or inactive users do not retain access longer than they should.
4. Prioritize security and compliance
Security must be at the heart of RBAC design. Following API dev portal security best practices helps you align with compliance frameworks such as GDPR, HIPAA, or industry-specific requirements.
To reduce the risk of data leaks or unauthorized system changes, implement least privilege principles, giving users only the access they need.
5. Optimize for developer experience
While security is non-negotiable, developer productivity is equally important. RBAC should not make the portal cumbersome to use.
Provide developers with self-service tools to request access, view their current roles, and understand why they may not have certain permissions.
Use a transparent system to enhance trust and ensure the portal continues to foster collaboration rather than becoming a roadblock.
Common RBAC challenges and how to overcome them
Implementing API developer portal role-based access control is essential to protect sensitive resources, streamline developer onboarding, and provide secure API developer portal access. However, many organizations face recurring challenges when designing and maintaining effective RBAC models.
Below are six common issues and practical strategies to address them.
1. Role explosion
As teams and projects expand, the number of roles can quickly grow out of control. For example, slight variations in responsibilities may result in dozens of overlapping roles. This makes API dev portal permissions management complex and harder to maintain.
To prevent role explosion, establish a standard set of core roles and extend them with attributes or policies rather than creating entirely new roles. Consider leveraging role hierarchies or attribute-based access control alongside RBAC. This approach reduces duplication while still giving granular control.
2. Role creep
Role creep happens when users accumulate API dev portal user roles and permissions over time, often because old roles are never revoked when responsibilities change. This creates unnecessary access and potential security risks.
To overcome this, schedule regular access reviews to identify and remove outdated or unused roles. To further minimize the buildup of excess permissions, automate de-provisioning when users switch projects or leave the organization.
3. Insufficient training
Even with a well-designed RBAC system, if administrators and developers don’t understand how roles and permissions work, errors can compromise secure API developer portal access. Misconfigured permissions could either block productivity or unintentionally expose sensitive APIs.
To avoid this mistake, provide continuous training and documentation for administrators and developers. You can also include interactive tutorials within the API developer portal role-based access control interface to help users apply RBAC correctly in day-to-day operations.
4. Balancing flexibility and security
Overly rigid role structures may limit productivity, while overly flexible ones may undermine security. Striking the right balance between the two is a recurring challenge.
Avoid this mistake by defining clear principles for API dev portal permissions management. Additionally, allow temporary, time-bound access for special cases instead of creating permanent roles.
5. Aligning RBAC with business processes
If RBAC structures don’t reflect how teams work, developers may bypass the portal's role-based access control system, leading to shadow IT and inconsistent policies.
This can be avoided by involving business and technical stakeholders in defining role requirements. You also need to map roles directly to business functions such as “API consumer,” “API publisher,” or “API administrator.” This ensures the system mirrors real-world responsibilities and enhances adoption.
6. Maintaining RBAC documentation
With frequent changes in team structures, projects, and APIs, keeping documentation accurate is a major hurdle. Outdated records can lead to confusion over API dev portal user roles and permissions.
Automate documentation wherever possible. For instance, integrate the RBAC system with version control or audit tools that log role changes. Keeping up-to-date records ensures compliance and simplifies troubleshooting when issues arise.
How to use RBAC to enhance API marketplace and monetization
If you want to use RBAC to boost API marketplace and monetization, follow these practical strategies:
Restrict premium APIs to certain roles
API marketplaces often include both free and premium endpoints. With RBAC, administrators can configure access so that only specific user roles, such as enterprise customers or paid subscribers, can consume high-value APIs.
This prevents unauthorized use while creating clear incentives for users to upgrade their subscriptions.
For example, free users may only call basic endpoints, while advanced analytics or financial transaction APIs are restricted to premium roles.
Implement role-based subscription models
RBAC allows marketplaces to tie subscriptions directly to roles. Instead of having a one-size-fits-all plan, users can subscribe to packages that unlock role-specific permissions.
A startup might be assigned a “developer” role with sandbox access, while a large corporation could have an “enterprise” role granting production-level API calls, higher request limits, and priority support. This structure makes it easier to segment customers and align pricing with usage needs.
Leverage role-specific API analytics
By applying RBAC, API providers can generate analytics that break down usage by role. This gives valuable insight into which groups are driving revenue, which endpoints are most used by premium customers, and where to improve monetization strategies.
For example, if “enterprise” users heavily use one API, the provider could introduce tiered pricing or add-on features for that role.
How DigitalAPI helps you implement API dev portals for better RBAC
Implementing an API developer portal for better RBAC can be a nightmare without the right tool.
Fortunately, DigitalAPI can streamline the implementation process for you.
Here’s how the AI-powered API management platform enhances RBAC in API developer portals:
Unified API catalog: DigitalAPI lets you connect multiple gateways into a single, AI-driven catalog—creating a “single source of truth” for all your APIs across environments. This unified API hub makes discovery intuitive and efficient. Developers can rapidly find the APIs they need thanks to AI-powered search and similarity detection, which also eliminates redundant APIs
For RBAC, a unified catalog allows you to apply access rules centrally, which ensures only the right roles or groups see specific APIs and guards against unauthorized discovery or misuse.
Access governance: DigitalAPI simplifies governance across the API lifecycle. It auto-generates documentation, tags metadata, enforces policies, helps with regulatory compliance, and integrates sandbox testing, all from one platform.
Through its API marketplace or portal, you can configure role-based access and version control, giving each role the precise permissions they need, whether to view, test, publish, or monetize APIs.
Analytics and insights: You gain a 360° view of API performance through real-time analytics on traffic, security, performance metrics, and business usage directly within DigitalAPI.
The platform also supports detailed usage analytics and reporting, segmented by service, user, or environment.
This enables you to monitor which roles or user groups are accessing which APIs, detect anomalies, assess compliance, and make evidence-based decisions on access levels or gateway policies. All of this helps you continuously fine-tune RBAC to match usage patterns and security demands.
FAQs
1. What is role-based access control (RBAC) in an API dev portal?
Role-based access control in an API developer portal is a security method that assigns permissions based on user roles rather than individuals.
Developers, admins, and business users each receive predefined access levels, ensuring only authorized users can view, manage, or consume APIs. This structure improves governance, security, and compliance within the API ecosystem.
2. How do I secure my API dev portal using RBAC?
You can secure your API developer portal with RBAC by defining clear user roles, mapping each role to specific permissions, and limiting access to sensitive APIs or features.
Admins manage role assignments, while regular audits help prevent privilege misuse. This minimizes security risks, ensures compliance, and strengthens governance across the portal.
3. Can RBAC be combined with API monetization?
Yes, RBAC can be combined with API monetization by restricting premium APIs to specific roles, enabling role-based subscription models, and delivering customized usage plans.
For example, only enterprise or paid-tier users can access high-value APIs, while basic roles remain limited. This approach balances security with revenue generation in API marketplaces.
4. What’s the difference between RBAC and ABAC in API portals?
RBAC assigns access rights based on predefined roles, making it simpler to manage but less flexible. Attribute-based access control (ABAC) uses dynamic attributes, such as user identity, location, or request context, to grant permissions.
While RBAC is easier to implement in API portals, ABAC provides finer-grained control for complex policies.
5. How often should I review roles and permissions in my API portal?
Roles and permissions in an API developer portal should be reviewed regularly, ideally quarterly or during major organizational or product changes.
Frequent reviews help remove outdated privileges, ensure compliance, and prevent unauthorized access.
Continuous monitoring paired with scheduled audits keeps your API portal secure and aligned with evolving business needs.
You’ve spent years battling your API problem. Give us 60 minutes to show you the solution.
.svg)

%20(1).png)



.avif)
