Blog
Top API Security Solutions and Tools for 2026: Protect Your APIs Against Emerging Threats
Updated on:

APIs now underpin digital banking, payments, healthcare exchanges, government services, and embedded finance. As attack surfaces expand across microservices, mobile backends, and partner ecosystems, API security has evolved from a tactical add-on to a board-level capability.
This brief highlights what matters in 2025, compares Top API Security Solutions or Tools, and shows how to deploy controls that cut enterprise risk while sustaining product velocity.
API security is non-negotiable in 2026
Modern enterprises ship APIs faster than governance can keep up.
“Only 19% of CISOs globally report full visibility and confidence in tracking their APIs.”
- The 2025 Salt Security CISO Report
Development speed, third-party integrations, and API reuse create blind spots that traditional WAFs and legacy gateways were never designed to solve.
Executive teams care because API abuse shows up as fraud losses, data exfiltration, outages that impact revenue, and costly incident response. On the upside, strong API security also enables safer monetisation, partner onboarding, and faster rollouts in regulated markets.
What is API security?
API security is the discipline of discovering and governing every API you expose, reducing risk before release, and protecting live endpoints from abuse across design, build, and run. In practice, it means keeping an accurate inventory, understanding what data each service handles, and enforcing strong authentication and authorisation.
During development, teams validate schemas and contracts, test negative paths, manage secrets well, and use CI/CD gates to stop issues early. In production, they watch traffic and behaviour, detect anomalies and business logic attacks, apply rate limits or virtual patches, and route clear alerts into the SOC.
Good programmes codify policy, least privilege, and change control, and they maintain a continuous posture across clouds. Data is handled with minimisation, encryption, residency choices, and auditable access. The aim is simple: expose only what is needed, only to authorised parties, only for as long as required, with sensible guardrails and end-to-end visibility.
Key features of effective API security solutions
Effective API security solutions deliver comprehensive lifecycle protection, reducing risk while preserving delivery speed and alignment with governance. The features that follow highlight what to prioritise in evaluation.
- Comprehensive discovery across gateways, clouds, services, and shadow APIs
- Posture management mapped to standards and policy guardrails
- Shift-left testing for API contracts, auth, and business logic
- Runtime protection covering exploits, abuse, and data exfiltration
- Bot and fraud signal correlation with API context
- Data protection and secrets hygiene across environments
- Clear analytics, forensics, and executive reporting
- Frictionless CI/CD, cloud, and gateway integrations
- Enterprise scale, role-based governance, and automation
Types of API security tools
A clear taxonomy of API security tools helps teams align their capabilities with risks and workflows, eliminating gaps and overlaps. It creates a shared language for architects, security, and developers to compare vendors, assign ownership, and measure coverage across the estate.
The categories below map to each stage of the API lifecycle, supporting consistent adoption across clouds, gateways, and teams. They also clarify integration points with identity, observability, and CI/CD, which reduces tool sprawl and accelerates onboarding without sacrificing control.
1. Discovery
Continuous, agentless inventory that surfaces every API across clouds and gateways, including shadow and zombie endpoints, so nothing dangerous hides in plain sight. Expect freshness SLAs, coverage metrics, and lineage to the systems where each API was observed.
- Inputs: gateway exports, traffic mirroring, cloud inventories, code and IaC scanning
- Outputs: unified catalog with owners, data classes, risk tags, and environment mapping
- Outcomes: reduced blind spots, faster incident scoping, and de-duplication of services
2. Posture management
Policy-driven checks that harden authentication, authorization, rate limits, and data exposure at scale, turning best practices into guardrails teams actually follow. Success looks like policy conformance trends, provable controls, and fewer risky defaults in production.
- Typical checks: TLS and mTLS, OAuth and scopes, CORS, PII exposure, versioning and deprecation
- Integrations: gateways, service meshes, ticketing, and policy repositories
- Outcomes: measurable hardening, fewer exploitable misconfigurations, audit-ready evidence
3. Shift-left testing
Contract and logic tests are wired into CI/CD that fail risky changes early, so insecure designs never make it to production. Mature programs track defect escape rates, fix times, and policy gates per pipeline.
- Typical tests: schema conformance, auth and RBAC paths, fuzzing, injection, abuse paths
- Integrations: IDE extensions, CI runners, PR status checks, artifact stores
- Outcomes: earlier detection, lower rework, safer releases
4. Runtime protection
Behavioural detection and positive security models that spot anomalies, block exploits, and contain blast radius without drowning operations in noise. Deployments span edge, gateway, sidecar, and out-of-band sensors to fit diverse architectures.
- Detects: BOLA and IDOR, injection, auth bypass, scraping, low and slow abuse
- Actions: inline enforcement, risk scoring, ticketing, and case management
- Outcomes: reduced MTTR, lower fraud and abuse impact, minimal alert fatigue
5. Bot and abuse mitigation
Signals that separate customers from scripts, stopping credential stuffing, scraping, and business logic abuse before it impacts revenue. Alignment with API context improves accuracy and reduces friction for legitimate traffic.
- Signals: device and network fingerprints, sequence anomalies, token integrity
- Controls: dynamic challenges, allowlists for partners, session binding
- Outcomes: fewer false positives, protected growth funnels, cleaner traffic
6. Data protection
Field-aware controls like masking, tokenization, and egress governance that keep sensitive data safe in motion and at rest. Programs use these tools to meet residency and compliance needs without blocking developer velocity.
- Capabilities: field-level detection, policy-based masking, DLP patterns, lineage
- Controls: schema annotations, egress policies, encryption posture
- Outcomes: smaller blast radius, compliant data handling, safer partner integrations
7. Secrets hygiene
Automated discovery and rotation of keys, tokens, and certificates, eliminating the long-lived credentials attackers love. Visibility extends into runtime to catch leakage in telemetry and error payloads.
- Sources: VCS history, CI artifacts, container images, logs, and traces
- Controls: auto revocation, vault integration, pre-commit and pipeline hooks
- Outcomes: fewer credential incidents, faster rotation, enforceable least privilege
8. Observability and forensics
Rich timelines, lineage, and replay that cut investigation time and turn incidents into concrete fixes teams can ship fast. Export-friendly data models support SIEM, SOAR, and analytics platforms.
- Features: session reconstruction, cross-service correlation, long-term retention
- Workflows: threat hunting views, developer-ready findings, change impact analysis
- Outcomes: faster investigations, durable fixes, measurable resilience gains
9. Integration fabric
Native hooks for gateways, service meshes, identity, SIEM, and SOAR that fit existing workflows instead of fighting them. A robust fabric keeps tools aligned with real traffic and real ownership.
- Connectors: Apigee, Kong, Istio and Envoy, AWS and Azure, Okta and OIDC
- Patterns: webhooks, streams, and bidirectional APIs for enforcement and evidence
- Outcomes: simpler operations, higher fidelity data, faster time to value
10. Governance and automation
Ownership, standards, and workflow automation that align product velocity with risk reduction so security scales with the business. Automation reduces manual toil and produces the audit trails leaders expect.
- Mechanisms: ownership maps, policy repositories, evidence capture, exception lifecycles
- Metrics: conformance trends, risk reduction per release, time to remediate
- Outcomes: predictable controls, transparent risk posture, scalable processes
Top API security solutions and tools for 2025
Security teams need a clear, current view of the top API security solutions and tools for 2025, with emphasis on coverage breadth, signal quality, deployment flexibility, and ecosystem fit. The intent is to help align vendor strengths with program goals and constraints before diving into individual options.
1. DigitalAPI.ai
A multi-gateway API management platform that unifies enterprise API discovery, governance, documentation, testing, and monetisation, with AI assistance to enforce metadata standards, detect duplicates, and scan for vulnerabilities. It centralises analytics across clouds and teams, and streamlines developer workflows and adoption.
Strengths (AI-powered Full Lifecycle API Defence)
- Multi-gateway, multi-cloud control with strong governance and developer experience
- AI-assisted metadata normalization, documentation autofill, and vulnerability scanning
- Built-in marketplace and monetization to safely grow partner and product ecosystems
- Real-time analytics from portfolio to endpoint across security, performance, and consumption
- CI/CD integrations for automated testing, policy gates, and release governance
- Role-based access, SSO, and segmented visibility for large, federated organisations
- AI-powered discovery and similarity matching to cut duplicates and drive reuse
- Developer portal with self-serve onboarding, sandboxes, subscriptions, and billing
Decision lens (Unified analytics‑driven governance)
- The strategy requires one control plane for both API lifecycle management and security controls
- There is a need to rationalise and catalog a large, distributed API estate
- Monetization and adoption are priorities alongside risk reduction
- Consistent policy enforcement and documentation standards must be applied at scale
- Reducing API sprawl via duplication detection and reuse is a measurable objective
- Leadership needs unified analytics linking product usage, operations, and security
- Multi-gateway, multi-cloud operations should be standardized without replatforming
2. Salt Security

A pioneer in API security that emphasises deep runtime context to detect and prevent attacks that exploit business logic. Strong at continuous discovery, posture, and runtime threat protection.
Strengths (Context‑aware API security)
- Time-sequenced detection that fingerprints attacker behaviour and surfaces logic abuse with high signal-to-noise.
- Continuous discovery of internal, external, shadow, and zombie APIs with sensitive data exposure insights.
- Attacker timelines and rich forensics that compress investigation time and speed response.
- Out-of-band deployment options that avoid code changes and minimise latency impact.
Decision lens (Actionable, automated remediation)
- Runtime visibility into business logic abuse and low‑and‑slow attack campaigns is a primary requirement.
- Fast identification of shadow/zombie APIs and sensitive data exposure is needed to reduce unknown risk.
- Alert fatigue is a problem, and context-rich, correlated detections are required to improve analyst efficiency.
- Out-of-band deployment with minimal operational friction is preferred over agent-based approaches.
3. Akamai API Security
Akamai’s platform incorporates Noname’s API security capabilities with Akamai’s edge footprint and bot defence. Delivers discovery, posture, testing, and runtime protection, with powerful global edge enforcement.
Strengths (Edge-native lifecycle API protection)
- Edge-native enforcement on Akamai’s global network combines scale, performance, and mature bot mitigation for resilient API defence.
- Lifecycle coverage spans discovery, posture, testing, and runtime through the integration of Noname’s capabilities into the Akamai platform.
- Multi-source inventory correlates code, traffic, uploaded specs, infrastructure-as-code, and inline components to close blind spots and speed ownership mapping.
- Managed service adds 24/7 monitoring and expert response for teams that need immediate coverage without adding headcount.
- Behavioural analytics baseline each API to surface logic abuse and anomalous usage that signature-only tools miss.
Decision lens (Code‑to‑prod visibility)
- Standardise API protection at the edge to unify web, app, bot, and API defences while minimising architectural change.
- Consolidate on an existing Akamai footprint to reduce vendor sprawl and achieve global enforcement with consistent policy.
- Close visibility gaps between code and production via repo scanning and multi-source inventory mapped to owners.
4. Traceable
An AI-powered platform blending application and API security that focuses on data exfiltration paths, API posture, and runtime attack detection, with strong lineage and data flow views.
Strengths (Data‑aware behavioural API security)
- Data-flow and lineage mapping that traces transactions from the edge to databases, exposing exfiltration routes and high-value assets.
- Continuous discovery of internal, external, partner, shadow, and zombie APIs with sensitivity classification.
- Behavioural analytics and anomaly detection that uncover business logic abuse and low-and-slow campaigns.
- Posture insights and drift detection that compare live behaviour to OpenAPI contracts for faster, targeted hardening.
- Real-time threat timelines and replay that compress investigation and response cycles.
Decision lens (Runtime logic‑abuse visibility)
- Data protection is a top priority and requires visibility into how sensitive information moves across services.
- Complex microservices and partner ecosystems need end-to-end lineage and ownership mapping.
- Security leadership wants one view that aligns AppSec and API security posture, testing, and runtime defence.
- Teams must reduce alert fatigue with high-fidelity, correlated detections and clear remediation guidance.
5. Cequence Security
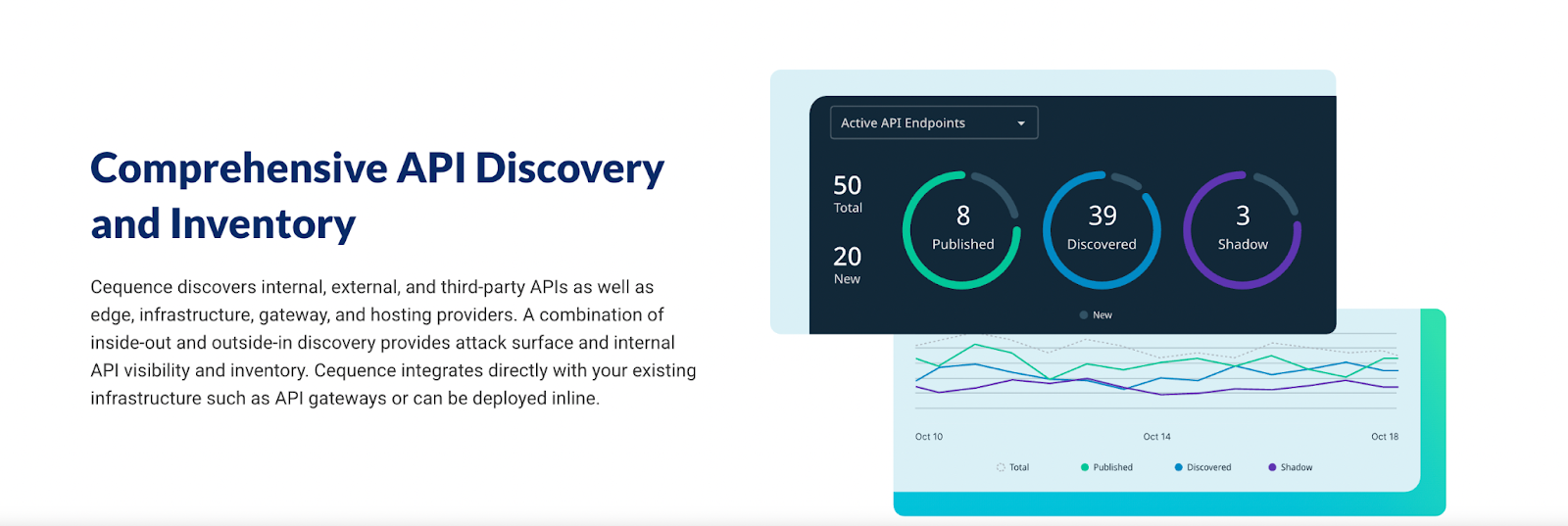
A unified platform that covers API security posture, runtime protection, and automated testing, with a strong heritage in bot and abuse mitigation applied to API traffic.
Strengths (Continuous API discovery)
- Continuous discovery of internal, external, partner, shadow, and zombie APIs with classification of sensitivity and risk.
- Outside‑in attack surface mapping to reveal exposed hosts, endpoints, and weak controls before attackers do.
- Posture management aligned to common API risks with customizable policies and automated remediation workflows.
- Automated API security testing, including spec generation and scenario creation, to block risky changes in pre‑production.
- Behavioural fingerprinting and bot mitigation that tracks retooling attackers and stops fraud, scraping, and ATO.
Decision lens (External and internal visibility)
- Automated fraud, account takeovers, scraping, and business logic abuse are primary API risks to contain.
- A single platform is needed to unify discovery, posture, testing, and runtime protection across teams.
- External attack surface visibility is required alongside internal runtime inventory and ownership mapping.
- Deployment flexibility (inline and out‑of‑band) is necessary to cover hybrid, multi‑cloud, and legacy estates.
6. 42Crunch

A developer-first platform focused on API contract security, shift-left testing, and enforcement from design through deployment, with runtime enforcement hooks via gateways.
Strengths (Contract‑driven API protection)
- OpenAPI audit with comprehensive security scoring and 300+ checks to raise contract quality early.
- Conformance scanning that validates live endpoints against the spec to catch logic and schema issues before release.
- Contract-derived runtime protection using a lightweight micro-API firewall that enforces a positive security model.
- Policy-as-code and reusable templates to push consistent standards across teams and services.
Decision lens (Auditable scoring and exceptions)
- Security must be designed in, with measurable design-time gates and CI/CD checks across all teams.
- The organisation is standardising on OpenAPI and needs policy-as-code to enforce it consistently.
- Reducing false positives and providing developer-friendly, actionable remediation is a priority.
- Runtime protection should be auto-configured from contracts rather than hand-crafted rules.
7. Data Theorem
A platform spanning mobile, web, cloud, and API security with continuous scanning, posture checks, and runtime protections, designed to bridge gaps across application layers.
Strengths (Risk‑validated automated testing)
- End-to-end coverage that ties mobile apps, web frontends, APIs, and cloud infrastructure into one risk picture.
- Continuous discovery and inventory of applications, APIs, and cloud resources to reduce blind spots.
- Automated testing across SAST, DAST, IAST, and SCA with an analyser engine that validates real risks.
- API attack path visualisation that links code issues to exploitable flows across services and cloud assets.
- Sensitive data detection and data-flow visibility that expose exfiltration routes and overexposed fields.
Decision lens (Unified device‑to‑data visibility)
- Mobile-to-API attack paths and data exposure require unified visibility from device to datastore.
- A single vendor is preferred to align AppSec and API security coverage and reduce operational overhead.
- Automated, continuous validation across the SDLC is needed to lower defect escape and speed releases.
- Attack path visualisation is required to connect code, APIs, and cloud assets for faster triage.
- SOC workflows benefit from integrated timelines, replay, and SIEM or SOAR connectivity.
- Minimal code change and agentless deployment are priorities for rapid rollout at scale.
Comparison snapshot
This snapshot presents a side‑by‑side view of leading options, highlighting coverage, signal quality, deployment flexibility, and ecosystem fit. It is designed for quick shortlisting by aligning capabilities with requirements and timelines.
7 Best practices for API security implementation
Modern API programs require consistent implementation from design through runtime, anchored in measurable controls and clear ownership. The best practices below focus on reducing risk, preserving developer velocity, and achieving repeatable outcomes across clouds, gateways, and teams.
- Establish a source of truth for APIs. Inventory across gateways, clusters, repos, and clouds. Assign ownership and lifecycle state. Treat unknown APIs as high risk.
- Gate design and contracts. Enforce OpenAPI standards, auth scopes, rate limits, and data minimization at design time. Fail fast in CI for violations.
- Validate in CI/CD. Add automated API security tests for auth, authorization, rate limiting, and sensitive data exposure before deployment.
- Protect at runtime. Use behavioural detection, positive security models, and anomaly detection to stop exploits and logic abuse. Tune for signal quality.
- Close the loop. Feed runtime findings back into design and posture policies. Automate fixes and track mean time to remediate by team.
- Govern secrets and data. Scan repos and images for keys. Tokenize or mask sensitive fields. Control egress paths and third-party calls.
- Measure outcomes. Track defect escape rate, incident mean time to detect and respond, shadow API reduction, and attack block rates. Report to the board in business terms.
Choosing the right API security tool
A sound choice maps tool capabilities to concrete risks, target architecture, and team workflows. Measurable coverage, low-noise detection, seamless integration, and total cost determine whether the program scales and endures.
Use the dimensions below to structure evaluation, proofs of concept, and final selection.
1. Operating model
Select a platform that matches your governance reality: centralised, federated, or partner-led. Define who sets policy, tunes detections, triages alerts, and approves blocks, with audit trails to back it up.
Look for multi-tenant admin, granular RBAC, versioned policies with safe rollout and rollback, and self-serve onboarding. If partners or an MSSP are involved, ensure secure access, shared runbooks, and clear SLAs.
2. Application architecture
Assume a mix of mobile, web, microservices, and partner APIs, and favor solutions that preserve end-to-end context. Validate discovery across gateways, meshes, serverless, containers, and even shadow APIs.
Ensure identity correlation across JWTs, OAuth/OIDC, mTLS, API keys, and service accounts, and demand protocol depth for REST, GraphQL, gRPC, WebSockets, and events. Choose deployment models that meet latency, fail modes, and multi-cloud needs.
3. Control coverage
Avoid chainable gaps by balancing discovery, posture, testing, runtime, and bot defences. Expect accurate inventory, schema inference, sensitive data classification, and exposure scoring. Strengthen posture with auth checks, least privilege, CORS and rate limits, and schema drift detection.
Shift left with contract tests, negative/fuzz testing, and CI gates; in runtime, require high-fidelity detections, virtual patching, adaptive rate limiting, and safe blocking, plus robust bot and supply chain controls.
4. Integration fit
Success hinges on integration, so test real pipelines. Confirm CI/CD and policy-as-code support, exemptions with expiry, and signing of tested specs. Ensure seamless fit with gateways and meshes, and clean hooks into observability, SIEM, and SOAR using structured logs and OpenTelemetry.
Map detections to identities and secrets, and in PoCs, measure time to value, tuning time, and friction.
5. Scalability and noise
Favor quality over quantity and demand proof it holds at scale. Measure false positive and negative rates on your traffic, learning period, drift handling, and suppression ergonomics. Track alert volumes, deduplication, grouping, and actionable guidance linked to routes and payload shapes.
Stress-test performance for throughput, latency, auto-scaling, and failure modes, and support fast tuning with feedback loops and environment-aware rules.
6. Data handling
Align with policy and regulator expectations without degrading protection. Require clear residency and sovereignty options, isolation model details, and auditable data paths. Configure retention and minimisation with redaction, tokenization or hashing, sampling, and selective payload capture.
Verify strong encryption, customer-managed keys, strict RBAC with SSO/MFA, immutable audits, and evidence for SOC 2, ISO 27001, GDPR, and HIPAA.
7. Team productivity
Choose tools that engineers like and leaders can measure. Improve developer experience with clear docs, IDE/CLI linting, PR spec diffs, and self-serve remediation hints. Prefer guardrails over hard gates, with accountable, auto-expiring exceptions and tight integrations with chat and issue trackers.
Model TCO over 12–24 months, and track outcomes like MTTR, critical service coverage, safe blocking adoption, and reduced abuse.
Future trends in API security
API security is entering a rapid evolution as scale, automation, and AI accelerate both attack capability and system complexity. Over the next 12 to 24 months, programs will emphasise measurable controls, contract awareness, and behaviour analytics, while aligning security with product and platform roadmaps.
Third-party dependencies and LLM-driven integrations will raise the bar for visibility, ownership, and continuous validation across environments.
AI-assisted defense
AI will accelerate detection by learning normal interaction patterns, correlating signals across identity, traffic, and code, and generating targeted policies from contracts and observed behaviour.
Expect automated triage, summary timelines, and suggested mitigations that shorten response while reducing noise. Human-in-the-loop reviews will remain essential for high-stakes actions, supported by explainable models, confidence scoring, and rollback paths.
Business logic testing at scale
Testing will move beyond payload fuzzing toward scenario-driven validation that simulates real user journeys, partner integrations, and abuse paths. Large-scale test orchestration will model stateful flows, conditional authorization, and rate policies, catching broken objects and function-level access that static rules miss.
Integration with design tools and CI will make logic checks routine, with synthetic data and shadow environments enabling safe, continuous exercises.
Positive security models
Contract-aware enforcement will shrink the attack surface by allowing only documented methods, paths, parameters, and schemas that match the source of truth. Schema-derived policies for REST, GraphQL, and gRPC will reduce handwritten rules and drift, with safe evolution through versioned contracts and staged rollouts.
Automated spec generation for legacy and shadow APIs will extend coverage where documentation is incomplete.
Unified application and API security
Convergence will continue as teams seek one view of threats across web, mobile, APIs, and the services that back them. Shared telemetry, correlated detections, and common response playbooks will connect code issues to exploitable API flows and cloud exposure.
The result is fewer silos, better prioritisation, and faster handoffs between security operations, developers, and site reliability engineering.
Secure monetization
As more organisations productize APIs, monetisation controls will intertwine with security posture and consumer trust signals. Expect adaptive access tiers, dynamic rate and entitlement decisions, and usage metering that respond to risk, device integrity, and partner reputation.
Transparent policies and verifiable attestations will help protect revenue, reduce fraud, and build confidence with customers and ecosystems.
The path forward
“Security is not a product, but a process.”
— Bruce Schneier, an American cryptographer and computer security professional
CISOs are moving from piecemeal defences to platform strategies that unify discovery, shift-left guardrails, and runtime protection. The solutions in this brief can all materially lower API risk. The right choice depends on the mix of controls needed, how teams build and release software, and where enforcement should live.
DigitalAPI.ai is compelling for leaders who want one control plane for the full API lifecycle, with security integrated into how APIs are designed, documented, discovered, and consumed. Dedicated API security platforms then add depth for runtime detection, bot and fraud defence, and advanced testing. Together, this combination reduces risk while accelerating digital outcomes.
FAQs
1. How does API security differ from web application security?
API security safeguards machine-to-machine traffic with granular authorization, data minimization, and contract integrity, while web app security focuses on user sessions and front-end flows; effective API defence also needs posture and runtime controls that understand schemas, scopes, and service-to-service trust.
2. Which tools protect against OWASP API Top 10 vulnerabilities?
Combine dedicated API security platforms (Salt Security, Traceable, Cequence), shift-left contract testing (42Crunch), and WAAP/gateways with schema validation (Cloudflare API Shield, Akamai) for OWASP API Top 10 coverage end to end.
3. Are open-source API security tools reliable?
Open-source API security tools can be reliable for targeted tasks (fuzzing, scanning, contract linting); pick commercial platforms for end-to-end, at-scale coverage, integrations, support, and outcome-focused analytics.
4. How can AI improve API security?
AI strengthens API security by correlating cross‑service behaviour to catch anomalies rules miss, recommending policy fixes, and automating documentation, metadata hygiene, and drift detection across large API estates.
5. Do small businesses need dedicated API security solutions?
Not initially. Basic gateway and cloud controls can suffice, but as API exposure, sensitive data, or partner integrations grow, a dedicated API security solution becomes necessary to protect trust and resilience.
6. What compliance standards should API security tools meet?
Align platforms and processes to enterprise assurance; prioritize data handling, governance, and auditability that match internal policy and local regulation instead of vendor-by-vendor claims.
7. How do API security platforms integrate with CI/CD workflows?
They plug into CI/CD to run OpenAPI linting, policy‑as‑code and auth/data‑exposure tests, enforce fail gates on violations, and return PR comments and machine‑readable reports for audit.
You’ve spent years battling your API problem. Give us 60 minutes to show you the solution.
.svg)

%20(1).png)





.avif)
