
Many organizations find themselves managing several different API gateways, whether due to regional requirements, different cloud providers, or business unit preferences. The idea of migrating everything into a single system is often overwhelming, expensive, and carries risk.
A smarter approach is to build a central control layer on top of your existing gateways. Start by mapping all your gateways and APIs, create a shared catalog, standardize your governance and policy practices, and put identity and access controls in one place.
With this setup, individual teams or locations can continue using the gateway they prefer while the organization still gains unified monitoring, traffic control, and API lifecycle oversight. The result is a flexible, scalable architecture with better governance without the disruption of a full migration.
Unlock your API architecture’s potential — Book your demo now
Managing multiple API gateways has become the norm, not the exception, for large enterprises. Whether due to acquisitions, department-level autonomy, or multi-cloud deployments, companies often find themselves juggling Apigee, AWS API Gateway, Mulesoft, and more. The traditional answer? Migrate everything to a single gateway. But that’s costly, disruptive, and often unnecessary.
In this blog, we explore how modern enterprises can manage multiple API gateways without migrating, using smart unification, centralised governance, and a composable control plane strategy. You’ll learn why multiple gateways exist in the first place, the challenges they create, and a practical step-by-step guide to solving them.
We’ll also share proven best practices for visibility, policy enforcement, and developer experience across distributed environments. So, if your organisation is struggling with API sprawl, inconsistent policies, or fragmented analytics, this blog will help you regain control without needing multiple platforms. Let’s dive in.
Why do businesses use multiple API gateways?
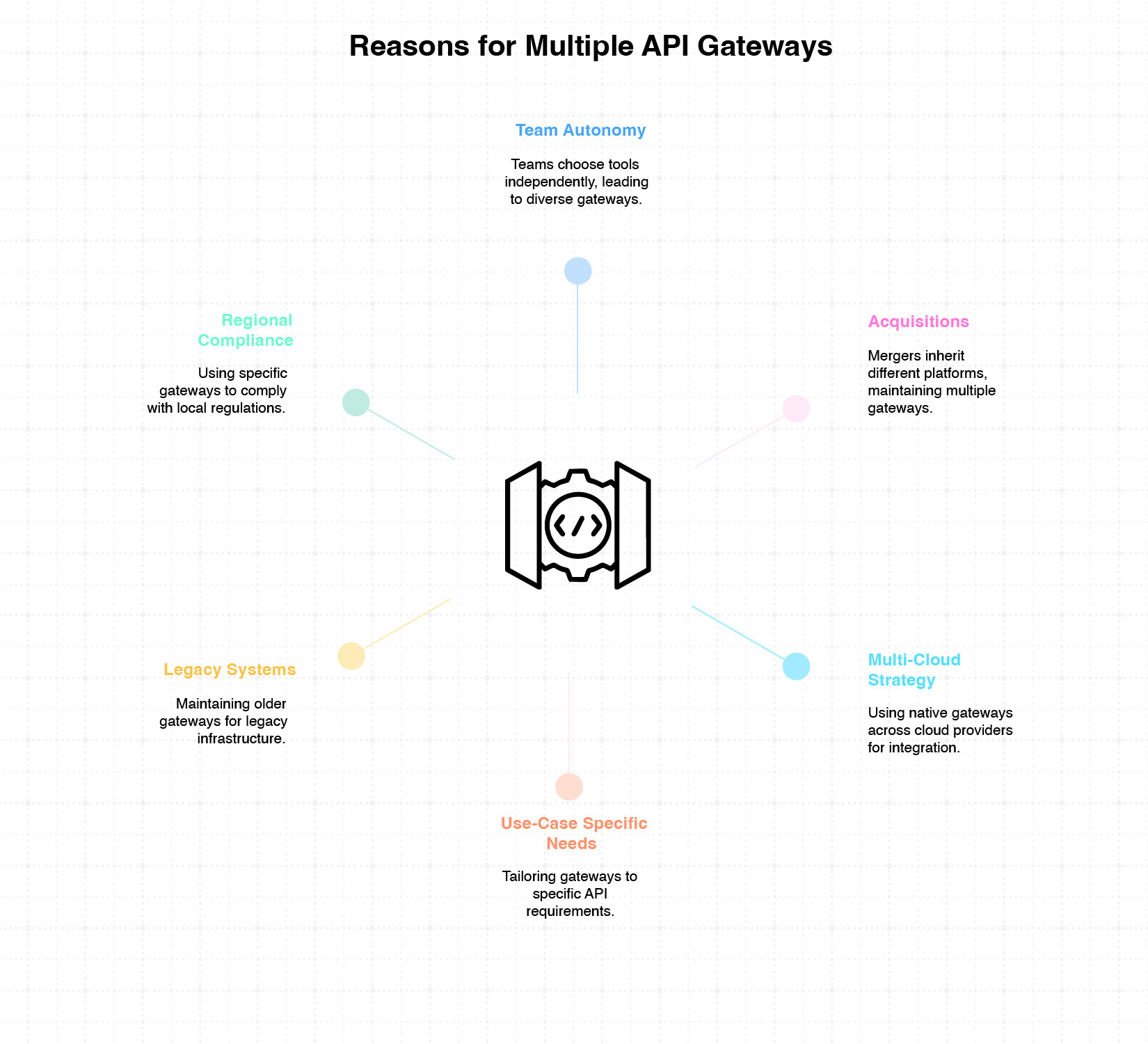
Most enterprises don’t deliberately plan to use multiple API gateways; it typically happens as a result of growth, acquisitions, or varying technical needs. As different teams adopt tools that suit their context, API sprawl becomes inevitable. Here are the most common reasons why organisations end up with multiple gateways in production:
1. Team autonomy and decentralised decision-making
In large organisations, different teams or business units are often empowered to choose their own tools. This autonomy enables faster delivery and innovation, especially in agile environments. However, it often leads to teams selecting different API gateways based on their local preferences or use cases, without a centralised strategy.
2. Acquisitions and mergers
When companies merge or acquire others, they inherit not just people and products, but also platforms. API gateways from the acquired entity continue to be used, either because migrating them is costly or because they serve specific legacy systems. As a result, the enterprise ends up managing a mix of gateway technologies over time.
3. Multi-cloud or hybrid cloud strategy
Many enterprises operate across multiple cloud providers such as AWS, Azure, or Google Cloud, as well as on-premise data centres. Native gateways in each environment are often used to ensure optimal integration, low latency, and region-specific compliance. This multi-cloud footprint naturally leads to gateway diversity.
4. Use-case specific technical requirements
Different API gateways excel in different areas; some are better suited for internal APIs, while others are optimised for partner onboarding or public API exposure. A team building integration-heavy workflows may opt for Mulesoft, while another team exposing microservices may prefer AWS Gateway. This results in gateway choices tailored to context, not consistency.
5. Legacy systems and staged modernisation
Older systems often rely on legacy API gateways that are deeply embedded into enterprise infrastructure. Replacing them outright is rarely practical due to cost, risk, or dependencies. As a result, newer APIs get built on modern platforms while legacy APIs continue to run on older gateways, creating a coexistence model.
6. Regional operations and regulatory compliance
Enterprises operating globally must often comply with local data protection laws and deployment constraints. In some cases, specific gateways are mandated or preferred in certain countries due to regulations, latency, or support. This regional variation leads to gateway sprawl that mirrors the company’s geographic footprint.

Top challenges in managing multiple gateways
Running multiple API gateways may feel like a practical compromise, but it often introduces a web of hidden complexities. Without a unifying strategy, visibility, control, and consistency begin to erode. Let’s look at the most common challenges organisations face in a multi-gateway environment:
- Lack of centralised visibility: With APIs scattered across different gateways, it becomes difficult to get a unified view of what exists, who owns it, and how it’s being consumed. This blind spot leads to duplicated effort, governance risks, and potential security gaps.
- Inconsistent security policies: Each gateway may implement its own approach to authentication, authorisation, and rate limiting. Ensuring that every API, regardless of where it’s hosted, follows uniform security protocols becomes an operational headache.
- Fragmented developer experience: Developers accessing APIs must navigate different documentation styles, onboarding workflows, and testing tools. This inconsistency increases learning curves, delays integration, and reduces overall API adoption.
- Difficulties in enforcing governance: Policy enforcement, such as naming conventions, data standards, or lifecycle rules, becomes hard to standardise. Without a shared control plane, enforcing governance across teams and tools becomes a manual, error-prone task.
- Redundant or duplicated APIs: Multiple teams may unknowingly build similar APIs on different gateways due to a lack of visibility. This not only wastes time and resources but also makes versioning and consolidation much harder over time.
- Disparate analytics and monitoring: With each gateway maintaining its own logging and metrics, getting a coherent picture of API performance or usage is nearly impossible. This hampers incident response, SLA tracking, and business insights.
- Complex onboarding for partners and consumers: External users often need to interact with APIs spread across multiple platforms, each with its own portal, credentials, and access process. This fragmented experience slows down partner integration and damages trust.
- Higher operational overhead: Maintaining multiple gateways means multiple teams, toolchains, and upgrade cycles. Licensing, compliance audits, and support models all become more expensive and harder to coordinate.
- Slower innovation cycles: Platform teams spend more time stitching together environments instead of enabling innovation. Time is wasted managing inconsistencies rather than building reusable components or improving developer tooling.
- Vendor lock-in risks and migration paralysis: Once APIs are deeply embedded in a gateway’s ecosystem, migration feels too risky or costly. This leads to lock-in, preventing the adoption of newer, more suitable technologies or governance approaches.
Can I unify APIs without migrating gateways?
Yes, it is entirely possible to unify APIs without migrating your existing gateways, and in many cases, it’s the smarter approach. Migration is often costly, time-consuming, and disruptive, especially for enterprises with legacy systems, region-specific deployments, or a large portfolio of APIs already in production.
Instead of consolidating everything into a single gateway, forward-thinking organisations are adopting a control plane approach. This involves layering a unified governance and visibility solution on top of your existing gateways. It doesn’t matter whether your APIs sit on Apigee, AWS, Mulesoft, or another platform; what matters is creating a single pane of glass through which you can discover, secure, and manage them consistently.
This method allows you to standardise access policies, streamline onboarding, and offer a seamless developer experience, all without touching the underlying infrastructure. It also ensures that different teams and business units retain the flexibility to use the tools best suited to their needs, while the enterprise maintains governance and control.
Ultimately, unifying APIs without migrating gateways is about decoupling control from execution. By building a central layer for visibility, governance, and documentation, you enable scale without friction and avoid the trap of endless replatforming. It’s a modern, pragmatic path for API-first enterprises.
Step-by-step guide to multi-gateway management
Managing multiple API gateways doesn’t have to mean chaos. With a structured approach, enterprises can gain full visibility, enforce governance, and enable consistency, without centralising infrastructure. Here are the steps to help you unify control across your API landscape.
1. Audit your existing gateways and APIs
Start by conducting a comprehensive inventory across all active gateways. Identify what APIs exist, where they reside, who owns them, and their current usage patterns. This helps you uncover duplication, deprecated APIs, and governance gaps, and sets the foundation for any unification strategy.
2. Establish a central API catalogue
Create a unified, searchable catalogue that indexes APIs from every gateway. This catalogue should include metadata, ownership details, usage policies, and lifecycle stages. A central catalogue improves discoverability, encourages reuse, and enables visibility at an organisational level, even if APIs are still running on different platforms.
3. Implement centralised governance policies
Define and enforce governance standards at the control plane level. These can include API naming conventions, security requirements (like OAuth or mTLS), rate limits, and versioning strategies. Use automation to apply policies consistently across gateways to reduce manual overhead and risk.
4. Unify access and identity management
Standardise how developers, partners, and internal users access your APIs. This can be achieved by integrating your gateways with a central identity provider (e.g. using OAuth 2.0, OpenID Connect, or SSO). Introduce a developer portal that handles access provisioning uniformly across different backends.
5. Integrate observability and monitoring
Use a control plane to aggregate metrics, logs, and traces across all gateways into a single observability dashboard. This allows platform teams to monitor performance, usage, and error rates holistically. It also enables proactive incident response and SLA tracking.
6. Streamline developer onboarding and experience
Unify the onboarding process by giving developers a consistent experience, one portal to discover APIs, get credentials, run test calls, and view documentation. Hide the underlying gateway complexity to ensure frictionless adoption and productivity.
7. Introduce lifecycle management and version control
Manage API lifecycle stages (draft, test, production, deprecated) across all gateways from one interface. Apply consistent rules for versioning, publishing, and retirement. This ensures that older APIs are not left unmanaged and newer ones meet enterprise standards before going live.
8. Enable internal and external marketplace models
Expose internal APIs to teams and departments in a structured, curated marketplace. Similarly, enable external partner access through a controlled publishing workflow. Both internal and external consumers should have a single source of truth for what’s available and how to consume it.
9. Apply security and compliance across the board
Monitor APIs for vulnerabilities, ensure encryption standards are met, and audit access logs regularly, across all gateways. Tools that offer centralised policy enforcement and compliance checks help mitigate risk without requiring migration or code changes.
10. Review, iterate, and mature your control strategy
Multi-gateway management is not a one-time project. Continuously assess how well your unified approach is working. Identify pain points, adapt governance rules, and evolve your developer experience based on feedback and platform growth.
7 best practices to manage multiple gateways
.jpg)
Most guidance on multi-gateway management stops at control planes and catalogues. But true operational excellence comes from deeper cultural, architectural, and strategic practices. Here are seven best practices that go beyond the obvious:
- Align gateways to business domains: Instead of structuring gateway usage around technologies or clouds, map them to business domains or value streams. For example, assign one gateway to “Payments” and another to “Customer Onboarding”. This improves accountability and aligns platform thinking with organisational goals.
- Design for graceful fragmentation: Recognise that some level of gateway sprawl is inevitable and even beneficial. Instead of eliminating it, design your architecture to embrace controlled fragmentation, with shared policies, interfaces, and observability layered above the diversity.
- Use tags and taxonomy to bring order to sprawl: Metadata is your best friend in a multi-gateway world. Implement consistent tagging for API ownership, domains, sensitivity, lifecycle stage, and consumer type. A good taxonomy helps you apply governance programmatically without manually chasing teams.
- Shadow your API supply chain for hidden dependencies: Use dependency mapping to trace how APIs rely on each other across gateways, especially internal vs. external flows. This visibility helps prevent cascading failures and supports better decisions when deprecating or versioning APIs.
- Build trust through scorecards, not mandates: Instead of forcing teams to follow governance rules, introduce non-blocking scorecards that rate APIs on documentation, security, versioning, and usage. Gamify maturity and let product teams own their APIs with pride, not pressure.
- Instrument KPIs across gateways to track platform ROI: Measure not just API usage, but how gateways contribute to outcomes like time-to-market, incident resolution time, or partner onboarding speed. These cross-gateway metrics help prove platform value and justify investment.
- Document your gateway strategy as an internal product: Treat your multi-gateway architecture like a product. Ensure it is complete with a vision, roadmap, stakeholder personas, and onboarding materials. Document not just the what, but the why behind design choices. This reduces internal confusion and builds long-term alignment.

Mastering multiple gateway management with DigitalAPI
At DigitalAPI, we understand that managing multiple API gateways is a major challenge. Enterprises today use multiple API gateways like Apigee, Mulesoft, AWS, and others across departments, regions, and cloud providers. So, rather than pushing for risky migrations, our platform enables you to unify API governance, discovery, and experience without replacing what already works.
Our unified control plane connects to all your gateways and brings your APIs into a single, searchable catalogue. Developers no longer need to hunt across siloed portals; they can discover, test, and consume APIs through one seamless experience. You also get centralised access control with consistent audit trails while ensuring that security policies can be applied uniformly, even if the APIs themselves live on different infrastructure.
We also offer in-depth analytics and observability, helping platform teams track adoption, usage, and performance across environments. So, whether you're onboarding a new partner, retiring a legacy gateway, or scaling developer self-serve, you have full visibility and control.
FAQs
1. Can I centralise governance without migrating all gateways?
Yes, you can implement a central control plane that connects to existing gateways like Apigee, AWS, and Mulesoft. This allows you to apply consistent policies, track usage, and streamline onboarding without moving the APIs themselves. It reduces operational risk while improving visibility, security, and compliance across the entire API estate.
2. What’s the best strategy for multi-cloud gateway management?
Use native gateways within each cloud for optimal performance and compliance, then unify them using a central control plane. This lets you apply consistent governance while preserving cloud-specific advantages. Keep identity, logging, and policy enforcement centralised to avoid fragmentation and maintain operational control across providers like AWS, Azure, and GCP.
3. How do I aggregate observability from multiple gateways?
Connect each gateway’s telemetry to a central monitoring platform such as Datadog, Grafana, or Prometheus. Standardise tagging across APIs and services to enable filtering by domain or environment. This setup offers unified visibility into performance, usage, and errors, supporting better incident response and more accurate service-level reporting.
4.Why do organisations end up with multiple API gateways?
Many companies start with a single gateway but then grow, merge, adopt multi-cloud or give teams autonomy. These factors lead to different business units choosing different gateways, acquisitions inheriting tech stacks, and regional or hybrid cloud requirements spawning new gateways.
5. Can you manage multiple API gateways without migrating to one?
Yes. Instead of migrating everything into a single gateway (which can be costly and disruptive), you can overlay a unified control plane on existing gateways. This means you keep each gateway in place but centralise governance, observability, and policy enforcement
You’ve spent years battling your API problem. Give us 60 minutes to show you the solution.
.svg)

%20(1).png)




.avif)
