
Did you know that a single overlooked API flaw can expose your entire system to attackers? As APIs become the backbone of modern applications, they’ve also become a goldmine for cybercriminals.
From unauthorised access and data breaches to session hijacking, API-related data breaches are on the rise.
So, how do you protect your API from becoming the next headline? It starts with API authentication.
Authenticating your APIs can be your first line of defence that ensures only verified users and systems can access your precious data.
But where do you begin?
In this post, we’ll explore what API authentication is, break down the most common methods, and share best practices you can use.
Key takeaways
- API authentication verifies the identity of users or systems before granting access to an API. It ensures that only authorised requests interact with your data, using methods like API keys, OAuth tokens, or JWTs.
- Without authentication, APIs are vulnerable to breaches, unauthorised access, and misuse. Proper authentication enhances security, regulates access, builds user trust, and reduces operational risks.
- Popular API authentication methods include API keys (simple but less secure), OAuth 2.0 (delegated access), JWT (self-contained tokens), and SSO (unified login). Each suits different security and usability needs.
- When choosing an API authentication method, consider security requirements, scalability, ease of implementation, and user experience. For sensitive data, OAuth 2.0 or JWT is ideal; for simplicity, API keys may suffice.
What is API authentication?
API authentication is the process of verifying the identity of a user or application before granting access to an API to ensure that only authorised requests interact with your data.
Essentially, API authentication involves generating and validating credentials like API keys, tokens, or OAuth flows to control who can access your endpoints.
How does API authentication work?
API authentication starts when a client sends a request with credentials like an API key, OAuth token, or JWT. The server validates these, checking for authenticity and permissions. If needed, a token is issued. Based on validation, access is granted or denied to ensure only authorised users or systems access the API.
We can explore further to understand how authentication in APIs works:
- Step 1: Client request: The process kicks off when a client (like an app or user) requests an API. Think of this as someone trying to enter a restricted area. They must present valid credentials, usually an API key, OAuth token, or a JSON Web Token (JWT). Without these, the server won’t even consider the request.
- Step 2: Server validation: Next, the API server checks those credentials. Are they valid? Are they expired? Do they have the right permissions? If the token uses OAuth 2.0 or OpenID Connect, the server might ping an external authorisation service to confirm everything checks out.
- Step 3: Token is generated (if needed): If the credentials are solid and a token hasn’t already been issued, the server will generate one (think of this as a temporary VIP pass). This token, packed with details like permissions and expiry, acts as a digital pass for the client. It helps streamline future requests to avoid repeated logins.
- Step 4: Access is granted or denied: Finally, the server makes its decision. If everything is valid, the client gets access to the requested resources. If not, they get an error message, usually a 401 Unauthorised or 403 Forbidden, telling them they’re not welcome without proper credentials.
It’s that simple.
But why should you authenticate APIs? You may ask.
Why is API authentication crucial?
API authentication is important because it ensures that only verified users and systems can access your API to protect sensitive data and prevent misuse. Without it, your API becomes an open door, one that anyone can walk through, including bad actors. That’s a risk no business can afford to take.
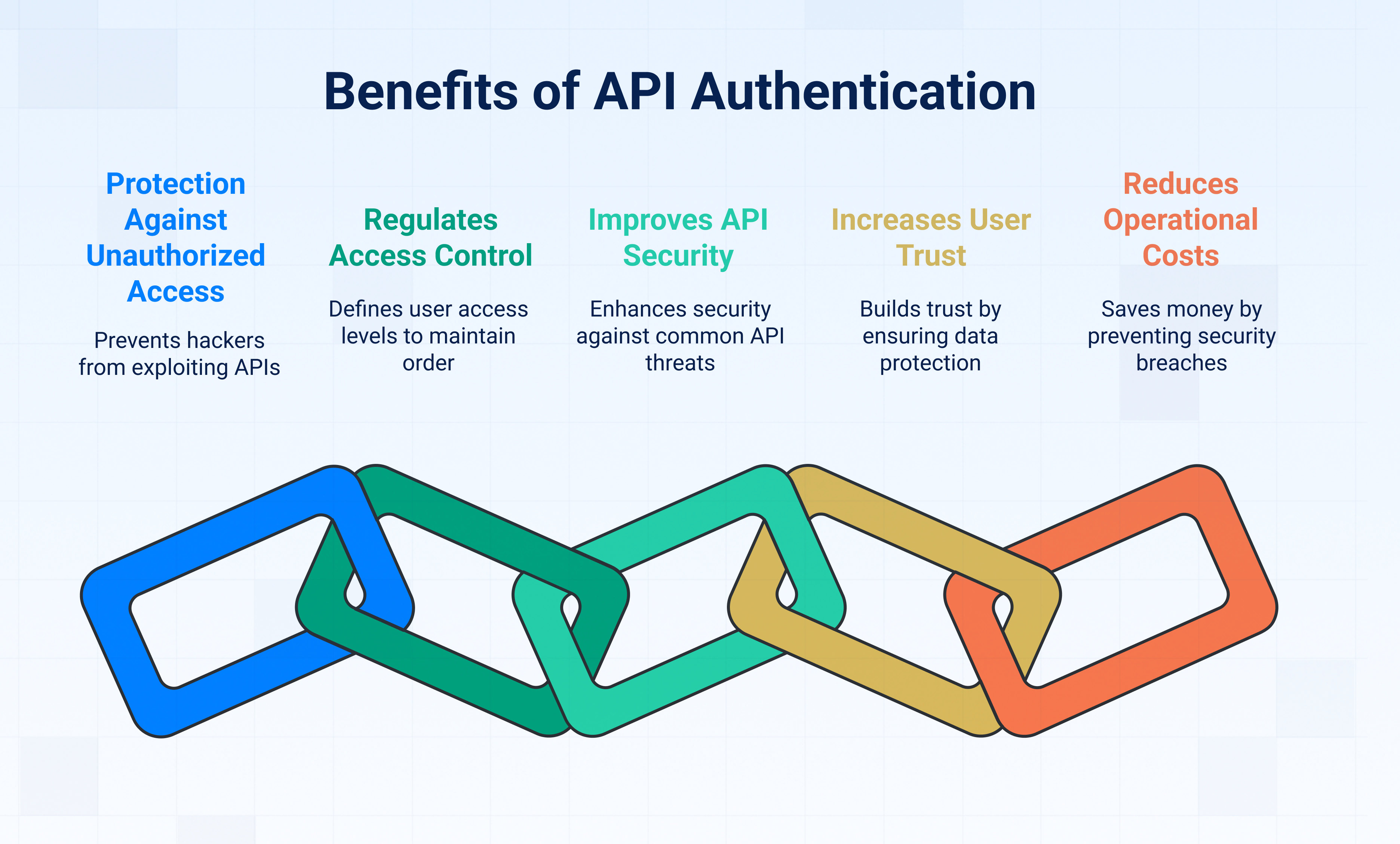
Well, here are the benefits of API authentication:
1. It protects against unauthorised access
Hackers love exploiting weak or missing authentication to steal data, inject malware, or crash systems. Proper authentication makes sure only legitimate users (ones who’ve proven who they are) can interact with your API. Whether it’s customers using your app or backend systems exchanging data, you want to keep out bad actors.
2. It regulates access control
Not every user should have the same level of access to your systems and data. API authentication works hand-in-hand with authorisation to define who can do what. For example, a regular user might only read data, while an admin can edit or delete it. By enforcing strict authentication, you prevent a freelancer from accidentally (or intentionally) messing with admin-level functions, which keeps your system orderly and secure.
3. It improves API security
As APIs become prime targets for attacks, authentication is the foundation of your API security. It allows you to verify user identity before allowing access, which prevents common threats like API abuse, credential stuffing, and man-in-the-middle attacks. Whether you use API keys, OAuth tokens, or certificates, a solid authentication strategy makes your API harder to break into.
4. It increases user trust
Would you trust an app that leaks data like a sieve? Neither would your users. API authentication shows that you take security seriously. When customers know their data is protected, whether it’s payment info or personal details, they’re more likely to engage with your API. Trust translates to loyalty, fewer support headaches, and a stronger reputation.
5. It reduces operational costs
Here’s something most people don’t think about: better API security saves money. When your API is locked down with proper authentication, you’ll face fewer data breaches, spend less time on damage control, and reduce the risk of regulatory fines. Authentication helps prevent unauthorised usage, which can otherwise drain resources and inflate backend costs.
6 Common API authentication methods and how they work
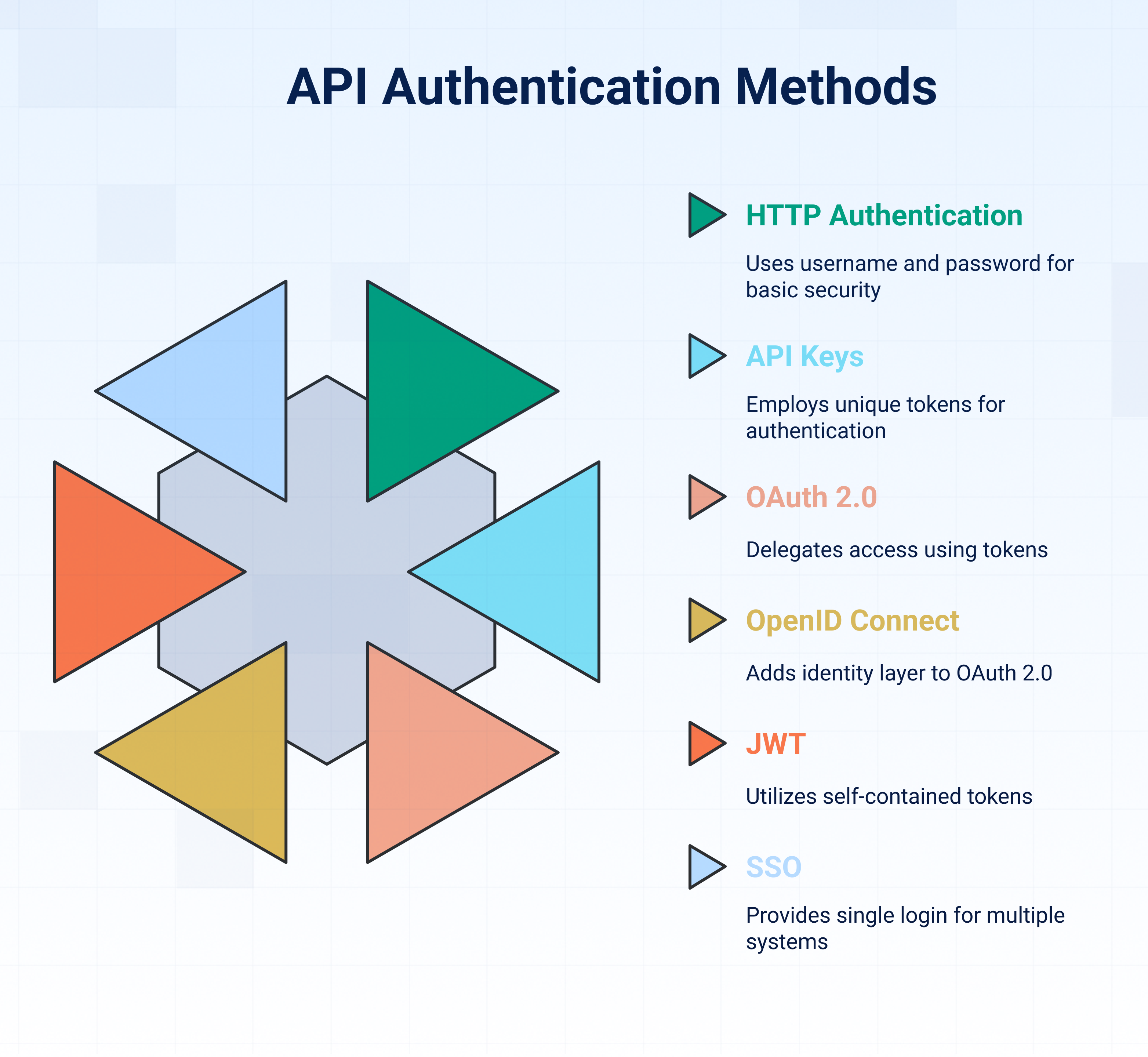
The most common API authentication methods include basic access authentication or HTTP authentication (username/password), API keys (unique tokens per user/app), OAuth 2.0 (token-based delegated access), OpenID Connect (identity layer on OAuth 2.0), JWT (self-contained tokens), and SSO (single login for multiple systems). Each secures APIs by validating user or app identities.
We'll break down what each method entails, including how it works so don’t worry.
1. HTTP authentication
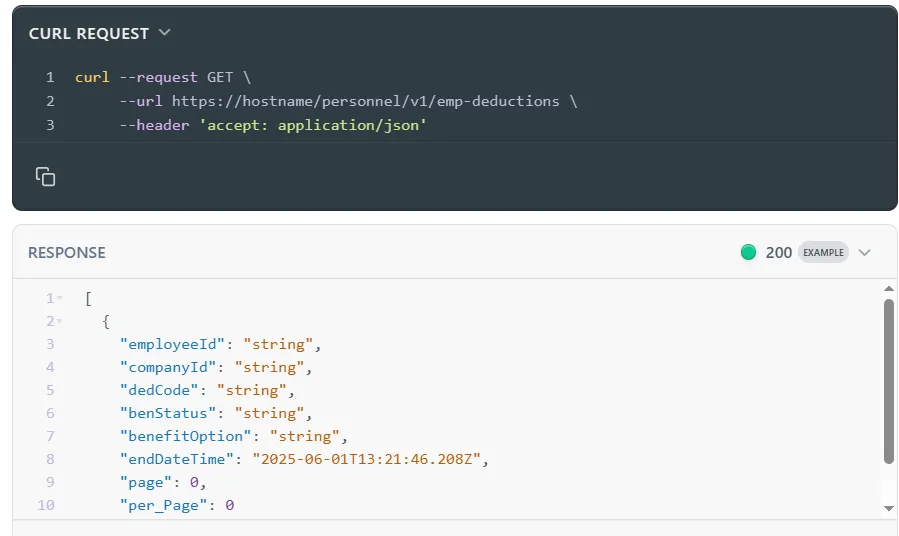
Basic or HTTP-based authentication is one of the earliest and simplest forms of API authentication, where a client sends a username and password with each request.
Here is how this API authentication method works:
- The application sends an HTTP request to the API with an Authorisation header with the word "Basic" followed by a base64-encoded string of username: password.
- The server decodes the credentials and checks them against a database.
- If the credentials are valid, the API returns the requested data. If invalid, it returns 401 Unauthorised.
An example of an API that uses basic authentication is the UKG Pro API. It uses this method to retrieve employee deduction data.
Advantages
- It’s easy to implement because there are no complex libraries or tokens needed.
- It works with all HTTP clients and tools.
- It is suitable for simple and low-risk systems.
Disadvantages
- It is insecure over HTTP since credentials are sent with every request and in plaintext.
- Compromised credentials may remain valid until you revoke them manually.
2. API Key authentication
API Key authentication involves using a unique identifier (API key) to authenticate requests instead of a username or password. This key acts like a password and is typically generated from a developer dashboard.
This API authentication method works as follows:
- The API provider issues a static key (e.g. abc123xyz).
- The client includes the key in requests via headers (such as X-API-Key: abc123xyz) and query parameters (like ?api_key=abc123xyz)
- The API checks if the key is valid and authorised.
- If valid, the API returns the requested data. If invalid, it returns 403 Forbidden.
Here is an example of an API by Teamtailor that uses this method:
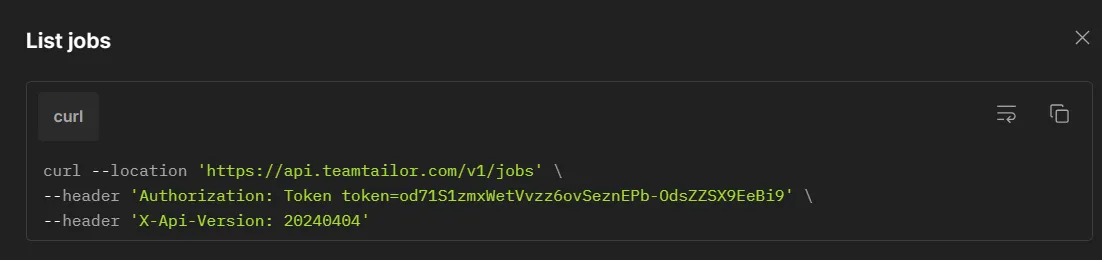
They use API key authentication to authenticate requests to their jobs API.
Advantages
- It’s simple to use and manage.
- It is great for internal apps or single-user services.
- It is better than HTTP authentication since there is no direct password exposure.
Disadvantages
- It is easily exposed if included in front-end code.
- It doesn’t provide built-in user-level permissions.
3. OAuth 2.0 authentication
OAuth 2.0 is an industry-standard protocol for authorisation. It enables applications to access user data from another service without exposing user credentials by using access tokens.
Here is how it works:
- The app sends the user to the OAuth provider (e.g., Google, GitHub).
- The user logs in and approves the requested permissions.
- The provider sends back an access token (short-lived) and optionally a refresh token.
- The app includes the token in requests (Authorisation: Bearer TOKEN).
- When the access token expires, the refresh token gets a new one.
QuickBooks (Intuit) uses OAuth 2.0 for secure third-party integrations.
Advantages
- There is no password sharing, hence users don’t expose credentials.
- Apps request only the data they need.
- It is widely adopted and secure.
Disadvantages
- It is complex to implement since it requires multiple steps to set up.
- It is vulnerable to phishing risks if redirect URLs are misconfigured.
4. OpenID Connect (OIDC)
OpenID Connect builds on top of OAuth 2.0 to add an authentication layer. It allows you to verify the identity of users and access basic profile information in a standardised way.
Here is how it works
- The app sends a request to an OIDC provider e.g., Google, Okta.
- The user authenticates, and the provider issues an ID token (a JWT containing user info).
- The app can also request an access token for API calls.
- The app validates the ID token’s signature and claims.
Salesforce API supports OIDC for SSO.
Advantages
- It is more secure than plain OAuth since it verifies user identity.
- Uses the same infrastructure as OAuth 2.0.
- It is standardised and widely supported.
Disadvantages
- It adds steps for identity checks, which makes it more complex than OAuth.
- It requires an identity provider, which makes it not ideal for simple APIs.
5. JSON Web Token (JWT)
JWTs are compact, self-contained tokens that store user identity and claims securely in JSON format. They’re often used for stateless authentication.
This method works as follows:
- The user authenticates and receives a signed JWT from the server.
- The JWT is stored (e.g., in localStorage or cookies).
- With every request, the client includes the token in the Authorisation header.
- The server verifies the token signature and decodes its contents.
Salesforce supports JWTs for secure server-to-server authentication.
Advantages
- This method doesn’t require server-side session storage.
- It is digitally signed to prevent forgery.
- It is compact and efficient for mobile or distributed systems.
Disadvantages
- Tokens cannot be revoked until expiration.
- It is a risky token that is exposed since it can be used until expiry.
6. Single sign-on (SSO)
SSO enables users to log in once and gain access to multiple applications or services without re-entering credentials. It typically uses protocols like SAML, OAuth, or OIDC.
Here’s how it works:
- The user authenticates with an identity provider (e.g., Google, Okta).
- The provider issues a session token.
- When the user visits another app, the provider confirms authentication.
- The app trusts the provider and grants access.
Examples of APIs that use this method include Facebook login, Google sign-in, and more.
Advantages
- There are no repeated logins required, which improves the user experience.
- It provides one place to manage access.
- It reduces password fatigue since there are fewer passwords to remember.
Disadvantages
- It is dependent on the provider; hence, if the provider is down, all apps are affected.
- Has a complex setup since it requires SAML, OAuth, or OIDC integration.
How to choose the right API authentication method
When choosing an API authentication method, focus on five key factors: security level, existing infrastructure, ease of implementation, scalability, and user experience. Each plays a role in determining how well your API performs, how secure it is, and how smoothly users interact with your application.
1. Consider the level of security you’re expecting
Security is the most important factor in API authentication. If your API handles sensitive data, like financial transactions, health records, or personal information, use strong authentication mechanisms like OAuth 2.0 or mutual TLS.
These methods support token expiration, scopes, and multi-factor authentication (MFA), making it harder for unauthorised users to gain access.
If your API is more basic and doesn’t store personal data, you might consider simpler methods like API keys. However, be aware that API keys, while easy to use, provide limited security since they’re static and can be easily compromised if exposed.
2. Pay attention to the existing authentication infrastructure
Before reinventing the wheel, look at what you already have. Are you using identity providers like Google, Microsoft Azure AD, or Okta? Leveraging existing systems can save you time and boost security through established protocols like SSO (Single Sign-On) and SAML.
For example, if your company already uses OAuth 2.0 for internal tools, extending that to your API makes a lot of sense. You’ll ensure consistency across services and reduce the learning curve for your team.
By aligning with your current architecture, you not only simplify development but also streamline future maintenance and support.
3. Consider ease of implementation
Let’s face it: Some authentication methods are trickier than others. OAuth 2.0, for instance, offers robust features but has a steeper learning curve and requires more setup. On the other hand, basic authentication or API keys can be implemented quickly, though they come with more risk.
If you're a small team or working under tight deadlines, a simpler method might be more practical in the short term. But don't let the ease of use tempt you into choosing something insecure for a high-risk use case. Balance your technical capacity with your long-term needs.
Keep in mind that easy doesn’t always mean best—it just means fast. Make sure you aren’t trading security for convenience.
4. Think about scalability
You want an authentication method that can grow with your application. As your user base increases, so do security threats and complexity. Some methods, like JWT (JSON Web Tokens), shine here because they allow stateless, scalable authentication, meaning the server doesn’t need to store session information.
OAuth 2.0 is also highly scalable and ideal for large applications with many users, services, or third-party integrations. On the flip side, methods like basic auth or static tokens may become unwieldy as your system scales and more keys are generated.
5. Prioritise user experience
User experience is often overlooked in technical decisions, but it shouldn’t be. If your API serves external users, you need an authentication method that doesn't feel like a roadblock. OAuth 2.0 with social logins, for instance, lets users sign in using accounts they already trust—like Google or GitHub.
For internal APIs, SSO and federated identity make it easier for employees to move between services without repeated logins. Poor authentication flows can frustrate users, create friction, and hurt adoption.
API authentication best practices
Protecting your APIs starts with strong authentication. Use secure methods, enforce access control, manage API keys carefully, enable logging, perform regular audits, implement MFA, encrypt sensitive data, and apply rate limiting. These best practices help prevent breaches, reduce attack surfaces, and ensure your APIs remain secure and reliable.
1. Choose strong and secure authentication methods
Let’s start with the foundation—authentication. You’re verifying that whoever’s trying to access your API is allowed to. The most common methods include OAuth 2.0, JWT (JSON Web Tokens), and API keys, but not all methods are created equal.
For high-security applications, OAuth 2.0 tends to be the gold standard because it allows granular permissions and token expiration. JWTs are useful for stateless authentication, and they work well in distributed systems.
Avoid relying solely on basic authentication or sending credentials in plain text. These outdated methods are easy targets for attackers. Instead, go with authentication that supports tokenisation, expiration, and encryption. If you’re building anything remotely sensitive, and think financial apps or healthcare tools, choosing the right method here is a must.
2. Implement access control
A user might be authenticated, but shouldn’t have access to everything your API offers. This is where role-based access control (RBAC) or attribute-based access control (ABAC) comes in.
Generally, authentication verifies the identity, whereas access control gives access permissions to what the user can do after getting in.
Using RBAC, for example, a customer support agent might only be able to view customer data but not update payment information.
Developers should implement least-privilege access by default users and systems should only get the permissions they need. This helps prevent lateral movement in the case of a breach.
3. Secure API key management
API keys are like your house keys. If you leave them lying around, anyone can walk right in. Always treat them as sensitive credentials.
First, never hard-code API keys directly into your source code or version control systems like GitHub. Use environment variables or secret managers like AWS Secrets Manager, HashiCorp Vault, or Google Secret Manager.
Second, rotate your keys regularly and revoke them immediately if compromised. Monitoring key usage also helps detect unusual patterns early. It’s not about if a key gets exposed, but when and how quickly you can respond.
4. Maintain detailed logs of API activity
Let’s face it, things go wrong. And when they do, logs are your best friend. Logging API activity helps you monitor user behaviour, spot anomalies, and trace the root of issues. Make sure your logs capture essential details like timestamps, IP addresses, request paths, response statuses, and user identifiers.
However, don’t log sensitive information like passwords or API keys. Use logging libraries that support redaction and secure storage. Centralised logging solutions like ELK Stack, Datadog, or Splunk make analysing API logs more efficient and effective.
5. Conduct regular security audits of your APIs
APIs evolve, and so do threats. That’s why security audits shouldn’t be a one-time event. Regularly test your API endpoints using automated tools like OWASP ZAP, Postman Security, or even manual penetration testing. Check for outdated dependencies, vulnerable libraries, and insecure headers.
These audits help you catch misconfigurations early before a bad actor does. If possible, include third-party assessments for an unbiased look into your API’s security posture. It's better to find and fix issues in-house than read about them in the headlines.
6. Implement multifactor authentication (MFA)
Passwords alone aren’t enough. They’re often reused, weak, or phished. MFA adds a crucial second layer, usually a temporary code from an app or device. If your API platform has a user interface for login (e.g., developer dashboards), enabling MFA can significantly reduce the risk of unauthorised access.
MFA also helps protect administrator accounts and third-party integrations. Even if a user’s password is leaked, that one-time code can stop attackers in their tracks. Encourage users to activate MFA and consider making it mandatory for critical actions or admin-level access.
7. Use encryption
Always use HTTPS (TLS 1.2 or higher) to encrypt data in transit. This ensures sensitive information like tokens, credentials, or personal data isn’t visible to anyone sniffing traffic.
Beyond transit, encrypt sensitive data at rest, whether it's stored in a database, log file, or cache. Use industry-standard encryption protocols and manage your encryption keys securely. If you’re handling regulated data (like HIPAA or PCI), encryption is a great idea.
What’s the difference between API authentication vs API authorisation?
API authentication is the process of verifying the identity of a user or application attempting to access an API. It's akin to showing your ID at a security checkpoint to prove who you are.
On the other hand, API authorisation comes after authentication and determines what an authenticated user or application is allowed to do. It's like having access to certain rooms in a building after proving your identity at the entrance. Authorisation defines permissions and access levels, often based on roles or scopes.
Here is a summary of the key differences between API authentication and API authorisation.
API authentication vs API authorisation: key differences
Common challenges with API authentication
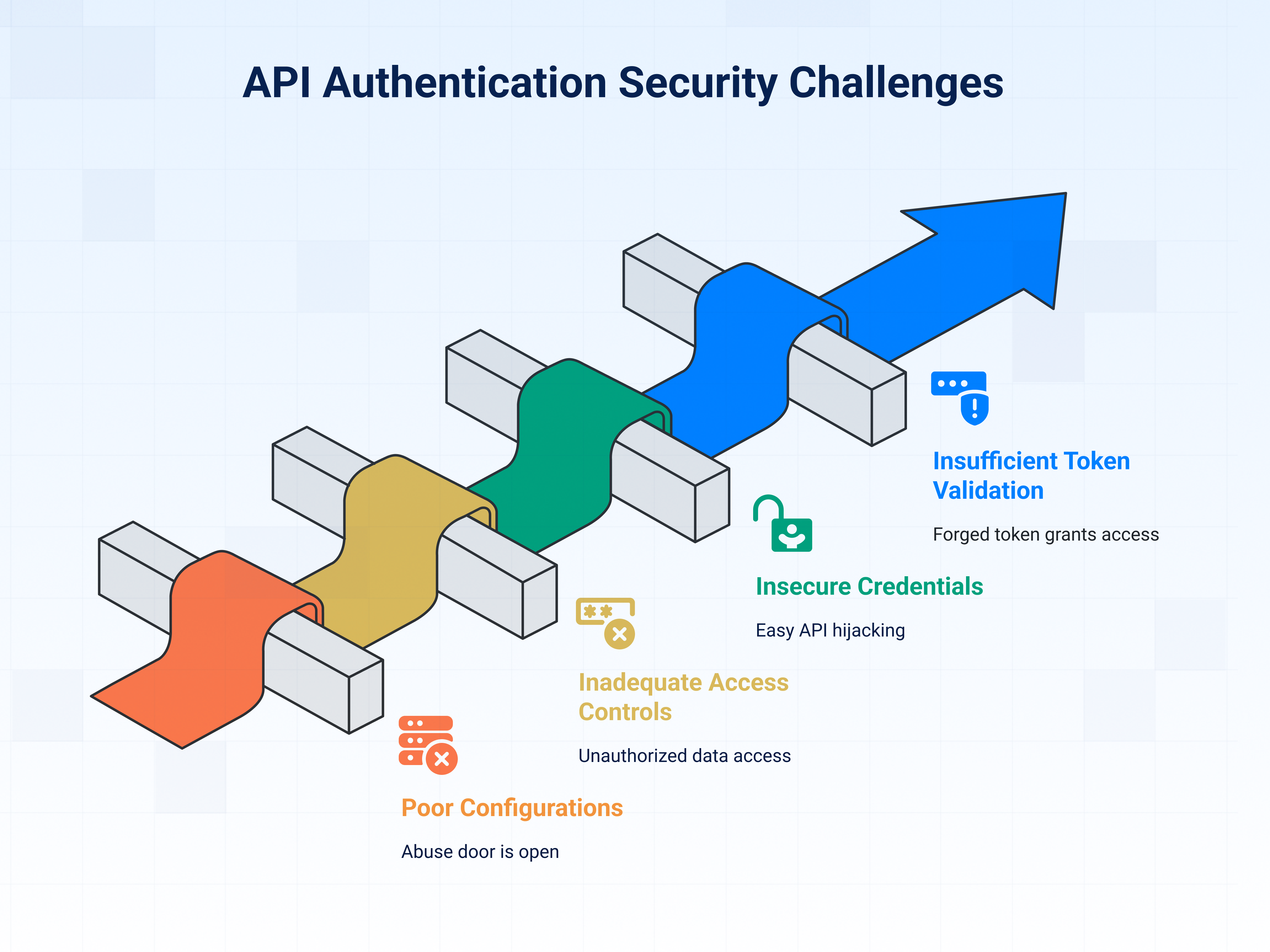
When working with APIs, authentication is a vital security step—but it's often easier said than done. Common challenges like poor configurations, weak access controls, insecure credentials, and token issues can create serious vulnerabilities.
1. Poor API configurations
Misconfigured APIs are like unlocked doors. You don’t notice the problem until it’s too late. Whether it's failing to enable rate limiting, not enforcing HTTPS, or exposing unnecessary endpoints, poor configuration choices open the door to abuse.
Some developers might leave debug settings on or forget to remove test endpoints before going live. These oversights can leak sensitive data or allow attackers to exploit the system. What’s more, inconsistent authentication methods across endpoints can confuse both users and developers, making the entire API harder to secure.
2. Inadequate access controls
Just because a user is authenticated doesn’t mean they are free to do everything as they wish. Access control defines who can do what, and failing to implement it properly leads to major risks.
Imagine giving all users admin-level privileges. Sounds like a disaster waiting to happen, right? Yet, this is exactly what happens when APIs don’t enforce role-based access controls (RBAC) or scopes.
Without proper permissions in place, a standard user could view or even change sensitive data they shouldn’t be touching. API keys or tokens should be tied to specific permissions to limit damage if they ever get exposed.
3. Insecure credentials
Let’s face it—storing API keys or tokens in plain text or hardcoding them into apps is asking for trouble. These shortcuts might save time during development, but they make it ridiculously easy for attackers to hijack your APIs.
Developers sometimes forget to rotate keys or disable old tokens, giving bad actors more time to wreak havoc. You wouldn’t leave your house key under the doormat, so why take the same risk with your API credentials?
4. Insufficient token validation
Tokens aren’t magic passes that should be trusted blindly. Without proper validation, an expired, stolen, or forged token can still grant access.
The key issue here is not checking the token’s signature, expiry time, issuer, or audience. This is especially risky with JSON Web Tokens (JWTs), where even a minor misstep in validation can lead to privilege escalation or data exposure.
Validating tokens at every request might seem repetitive, but it’s essential to maintain trust in your API’s security posture.
Simplify API authentication with DAC
Managing API authentication securely and efficiently is critical for modern applications but without the right software, it can be challenging.
That’s where DigitalAPI becomes helpful.
DigitalAPI offers a robust solution for managing API authentication to ensure secure and streamlined access across your digital ecosystem. Here’s how DAC helps:
- Centralised API gateway: Enforces consistent authentication mechanisms like OAuth 2.0, JWT, and API key validation across all APIs to reduce vulnerabilities and simplify control.
- Advanced policy enforcement: DAC allows you to define and apply fine-grained authentication and authorisation policies per API, ensuring only the right users and apps gain access.
- Integrated Developer Portal: The API management platform streamlines credential management by enabling developers to easily request, manage, and revoke access tokens or API keys through a secure, self-service interface.
These capabilities make DigitalAPI a powerful choice for organisations looking to strengthen API security, accelerate developer onboarding, and maintain governance across distributed systems.
Want to see how DigitalAPI works? Book a free demo here today!
FAQs
1. What is the most secure API authentication method?
The most secure API authentication method today is OAuth 2.0 combined with OpenID Connect. It lets users log in through trusted identity providers without exposing passwords. It’s secure, flexible, and widely adopted, which makes it great for protecting sensitive data while keeping things smooth for both developers and users.
2. Do all APIs need authentication?
Not all APIs require authentication, but most should. If an API handles private or sensitive data, you’ll want some form of authentication to prevent unauthorised access. Public APIs might skip it, but adding even basic auth helps control usage and protect your infrastructure from abuse or overuse.
3. How do I pass an API authentication token?
You usually pass an API authentication token in the request header using the "Authorisation" field. A common format is: Authorisation: Bearer YOUR_TOKEN_HERE. This way, the server recognises who you are and what you're allowed to do without exposing your credentials in every request.
You’ve spent years battling your API problem. Give us 60 minutes to show you the solution.
.svg)

%20(1).png)


.avif)
